| Hardware Security Modules (HSMs) are electronic devices using various hardware protection schemes against unauthorized reading of the secret...
More about encryption (10)
| We all understand the need to encrypt messages and documents. But how did we get to today's encryption technologies, how do they work, and h...
| In the previous article in our series of projects on DIY highly secure communications [1], it was shown how to build a secure tamper-evident...
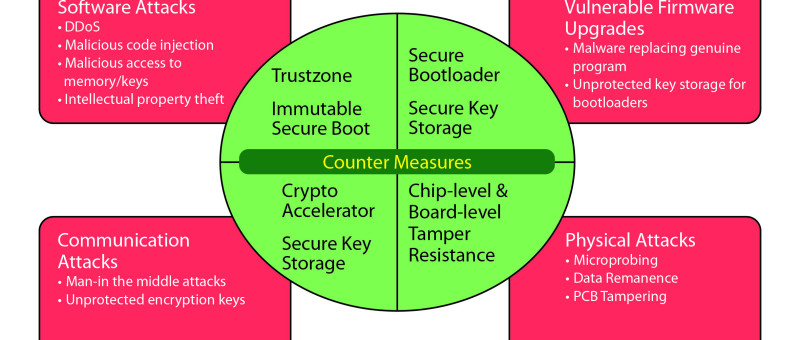
| The IoT has the potential to create huge value from the real-time data collected from sensors and embedded systems in any network. But with...
| The integrity of embedded systems can be ensured through the use of cryptographic methods in a clearly defined process and a secure hardware...
| Seen here on its slow way to launch, but actually launched in the Gobi desert on 16 August and carried by a Long March-2D rocket, is Micius,...
| In the same week British Prime Minister Cameron proposed a ban on encryption “to keep our people safe”, Der Spiegel revealed that the NSA us...
| CyanogenMod, a community built distribution of Android, has teamed up with Open WhisperSystems to provide user friendly cross-platform encry...
| As the recent NSA leaks highlight the importance of privacy enhancing tools, Adafruit presents the Onion Pi. This DIY project explains how s...
| Privacy enhancing tools have a bad reputation when it comes to usability. Nathan Freitas of The Guardian Project demonstrated easy to use ap...