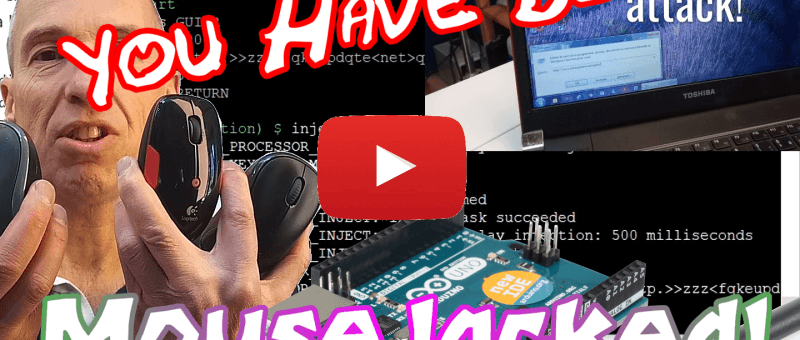
| Wireless mice, especially the older ones, can turn well-protected computers into vulnerable systems. Cheap and readily available tools like...
More about Hackers (6)
| Wireless mouses, especially the older ones, can turn well-protected computers into vulnerable systems.
| A small Raspberry Pi computer has been used to steal data from the Jet Propulsion Lab (JPL) of NASA. A report states that about 500 MB of da...
| The IoT has the potential to create huge value from the real-time data collected from sensors and embedded systems in any network. But with...
| Chaos Communication Congress: Engaging Technology and Its Impact on Society High-level talks about technology as well as reflections on the...
| The Exceptionally Hard & Soft Meeting (EHSM) explores the outer limits of open source hardware and software. The conference takes place in B...