Cyberweapons are putting us all in harm's way
May 17, 2017
on
on
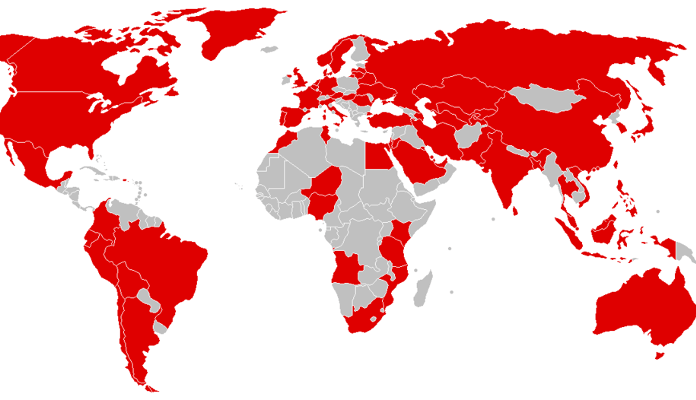
The cyberattack that hit the world on Friday May 12th is a stark reminder that governments need to rethink cybersecurity policies. The chaos in British hospitals and other organizations shows that a secure internet is critical to our way of life. Government resources should therefore go to defending the global network rather than attacking it.
Intelligence agencies like the NSA (US) and GCHQ (UK) have a dual mandate of defending the national networks as well as attacking those of adversaries. These two directives are incompatible in a global system: weaknesses exploited to attack an adversary are making the home networks equally vulnerable.
This became abundantly clear during Friday’s WannaCry ransomware attack. The attacker appropriated a cyberweapon developed by the NSA called EternalBlue and set it loose on the world.
EternalBlue exploits a vulnerability in Microsoft operating systems. The NSA has known about the existence of the weakness for years. The agency could have notified Microsoft back then, enabling the company to close the security hole and protect its millions of users. Instead, the NSA opted to weaponize it.
The NSA did warn Microsoft in the end, after it realized it had lost control over the cyberweapon. In response, the software company issued a patch on March 14. But many organizations had not updated their systems at the time of the attack.
One take-away from the attack is the importance of keeping systems up-todate (although that is not as easy as it sounds for complex IT infrastructures). But the more important issue is: how did it come to pass that the British have to defend their National Health Service against a cyberweapon created by their American allies?
Had the NSA notified Microsoft at the time of discovery, hospitals would have had years not weeks to patch their systems. More importantly, if the NSA would have prioritized defense over offense – that is: disclosing the flaw rather than exploit it - this cyberweapon would not have existed in the first place.
90% offensive
The surveillance and hacking tools developed by the NSA and its likes, make the entire internet less secure. At the same time our critical infrastructure is increasingly dependent on the internet. Hospitals, power plants, transport systems, if the internet goes down, they’re going down with it. In the dual mandate given to intelligence agencies the defensive role is therefore at least as important as the offensive one. But at the moment, cybersecurity policies of many countries are extremely biased toward the offensive:
‘Across the [US] federal government, about 90 percent of all spending on cyber programs is dedicated to offensive efforts, including penetrating the computer systems of adversaries, listening to communications and developing the means to disable or degrade infrastructure’, Reuters reported in March.
Microsoft, at least, is fed up with having to defend citizens against cyberweapons created by their own governments. In response to the WannaCry attack it said: ‘The governments of the world should treat this attack as a wake-up call. They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world. We need governments to consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits. This is one reason we called in February for a new “Digital Geneva Convention” to govern these issues, including a new requirement for governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit them.’
Image: Countries initially affected in WannaCry ransomware attack. Courtesy: Wikimedia Commons.
Intelligence agencies like the NSA (US) and GCHQ (UK) have a dual mandate of defending the national networks as well as attacking those of adversaries. These two directives are incompatible in a global system: weaknesses exploited to attack an adversary are making the home networks equally vulnerable.
This became abundantly clear during Friday’s WannaCry ransomware attack. The attacker appropriated a cyberweapon developed by the NSA called EternalBlue and set it loose on the world.
EternalBlue exploits a vulnerability in Microsoft operating systems. The NSA has known about the existence of the weakness for years. The agency could have notified Microsoft back then, enabling the company to close the security hole and protect its millions of users. Instead, the NSA opted to weaponize it.
The NSA did warn Microsoft in the end, after it realized it had lost control over the cyberweapon. In response, the software company issued a patch on March 14. But many organizations had not updated their systems at the time of the attack.
One take-away from the attack is the importance of keeping systems up-todate (although that is not as easy as it sounds for complex IT infrastructures). But the more important issue is: how did it come to pass that the British have to defend their National Health Service against a cyberweapon created by their American allies?
Had the NSA notified Microsoft at the time of discovery, hospitals would have had years not weeks to patch their systems. More importantly, if the NSA would have prioritized defense over offense – that is: disclosing the flaw rather than exploit it - this cyberweapon would not have existed in the first place.
Subscribe
Tag alert: Subscribe to the tag Elektor Ethics and you will receive an e-mail as soon as a new item about it is published on our website! 90% offensive
The surveillance and hacking tools developed by the NSA and its likes, make the entire internet less secure. At the same time our critical infrastructure is increasingly dependent on the internet. Hospitals, power plants, transport systems, if the internet goes down, they’re going down with it. In the dual mandate given to intelligence agencies the defensive role is therefore at least as important as the offensive one. But at the moment, cybersecurity policies of many countries are extremely biased toward the offensive:
‘Across the [US] federal government, about 90 percent of all spending on cyber programs is dedicated to offensive efforts, including penetrating the computer systems of adversaries, listening to communications and developing the means to disable or degrade infrastructure’, Reuters reported in March.
Microsoft, at least, is fed up with having to defend citizens against cyberweapons created by their own governments. In response to the WannaCry attack it said: ‘The governments of the world should treat this attack as a wake-up call. They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world. We need governments to consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits. This is one reason we called in February for a new “Digital Geneva Convention” to govern these issues, including a new requirement for governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit them.’
Image: Countries initially affected in WannaCry ransomware attack. Courtesy: Wikimedia Commons.
Read full article
Hide full article


Discussion (0 comments)