| In 2025, AI made it effortless to deploy code you didn’t fully understand. Now the consequences are catching up: instability, security vulne...
More about embedded security (14)
| Elektor TV delivered a breakout year in 2025, generating 5.9 million views while rapidly expanding its global engineering audience through h...
| As eeNews Europe reports, 2025 saw chip and EDA giants race to consolidate as next-gen AI data center silicon demanded new levels of power a...
| As embedded and IoT systems grow more connected and critical, their security risks extend well beyond traditional software threats. This art...
| The age of treating embedded security as a "nice to have" is officially over. Every network-connected device is now a security-relevant syst...
| On December 3, 2025, Elektor is hosting a conference on post-quantum cryptography and its significance for embedded and IoT systems. Ahead o...
| With the Elektor online conference “Zephyr – The Open RTOS for Future Devices” approaching this November, we caught up with speaker Pierre L...
| Raspberry Pi RP2350 A4 stepping release fixes security vulnerabilities, resolves GPIO erratum, and introduces RP2354 variants with integrate...
| Engineer Aedan Cullen hacked Raspberry Pi’s RP2350 microcontroller, exposing flaws in its security. Results of the $20K contest will be anno...
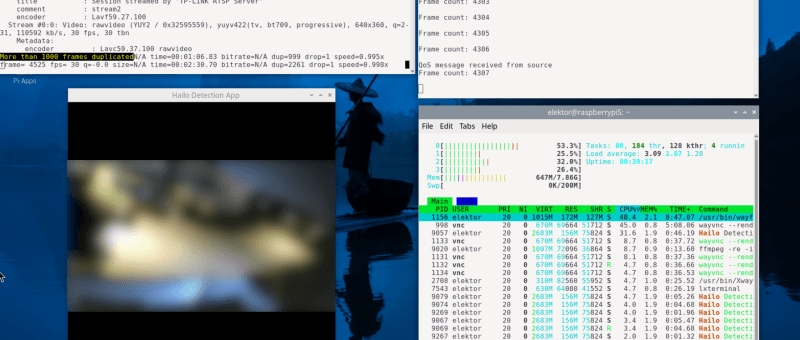
| AlertAlfred is an AI-powered security system built on a Raspberry Pi 5 and the Hailo 8L module, designed to detect people in a CCTV feed in...