Abandoned Zombies Haunt the Net
August 07, 2015
on
on
Six years after the Conficker botnet has been taken down, nearly a million machines remain infected. These vulnerable machines are easy prey for other botnets, researchers of Delft University of technology found.
Hadi Asghari, Michael Ciere and Michel van Eeten examine which measures are most successful to fight a malware epidemic that has spread across the globe in their Open Access paper Post-Mortem of a Zombie: Conficker Cleanup After Six Years. They paid special attention to the effect of national anti-botnet centers.
The Conficker botnet – a network of computers infected with malware that enables an attacker to take control of the machines - is one of the largest ever found on the internet. Discovered at the end of 2008, Conficker exploited a vulnerability present in all Windows versions that existed at the time. Even though Microsoft had released a patch for the vulnerability around the time of the discovery of Conficker, the botnet continued to grow at an alarming rate.
A consortium of parties including Microsoft and ICANN established the Conficker Working Group (CWG) to fight the botnet. When Conficker was used to sell fake anti-virus software in 2009 for between $50 – 100 duping nearly a million computer users, Law Enforcement joined the fray. The CWG eventually neutralized the botnet by cutting off communications between the operators and the zombie machines forcing the botherders to abandon their botnet. In 2011 several arrests in different countries were made in response to the fake anti-virus scheme.
Healthy global network
But even though the victim machines are no longer part of a zombie army, nearly a million of them remain infected. In June 2014 Conficker was still listed as the 6th largest known botnet. Leaving so many computers vulnerable is detrimental to the overall health of the internet.
Infected computers can be “a magnet for other threats”, write Asghari and colleagues in their paper. “The recent sinkholing attempt of [the botnet] GameoverZeus, for example, is more a tug of war between attackers and defenders, rather than definitive takedown action. The bots that remain after a takedown of C&C [command-and-control] infrastructure may also attract other attackers, as these machines remain vulnerable and hence can be re-compromised.”
With the aim to facilitate better large-scale cleanup efforts of infected computers in the future, the Delft team examined which factors contributed to fighting the Conficker plague. They took a dataset that logs Conficker bots on a daily basis, and looked at how quick the malware spread, the infection levels at peak, and the cleanup rate. They sorted it by country to differentiate between factors like the existence of anti-botnet initiatives, broadband access, piracy rates and the ICT development index.
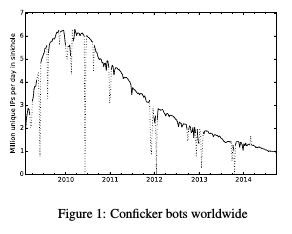
Source: Post-Mortem of a Zombie: Conficker Cleanup After Six Years
National anti-botnet centers
An increasing number of countries are setting up national anti-botnet centers. These are often public-private partnerships with a central role for Internet Service Providers because of their proximity to end users. These centers are considered a best practice but little research has been done to quantify their success rate.
To their own surprise, Asghari and colleagues found no correlation between the existence of such a national center and the spread or demise of Conficker. “It is somewhat surprising, and disappointing, to see no evidence for the impact of the leading remediation efforts on bot cleanup”, they write.
Piracy and proficiency
The team did find two other factors that have a significant impact on both the growth rate and the cleanup rate. In countries with a high level of pirated copies of the Microsoft operating systems, the malware spread more easily. This outcome they find far less surprising: “In addition to the fact that pirated software might include malware itself, users running pirated OS’s often turn off automatic updates, for fear of updates disabling their unlicensed software — even though Microsoft consistently states that it will also ship security updates to unlicensed versions of Windows.”
The other factor is the ICT development index. This internationally established benchmark indicates ICT maturity based on parameters such as digital infrastructure and literacy. Countries that score high on the index were better equipped to keep Conficker at bay.
For the good of all
This is not so surprising when making the analogy with public health. High quality health care infrastructure and knowledge of and access to nutritious food results in a more healthy population. And just like humanity would be better off if all people could enjoy these benefits, so it is for computers:
“The fact that peak infection levels strongly correlate with ICT development and software piracy, suggests that botnet mitigation can go hand in hand with economic development and capacity building. Helping countries develop their ICT capabilities can lower the global impact of infections over the long run”, Asghari, Ciere and Van Eeten conclude.
Image: Norse: Real-time global cyberattacks map
Hadi Asghari, Michael Ciere and Michel van Eeten examine which measures are most successful to fight a malware epidemic that has spread across the globe in their Open Access paper Post-Mortem of a Zombie: Conficker Cleanup After Six Years. They paid special attention to the effect of national anti-botnet centers.
The Conficker botnet – a network of computers infected with malware that enables an attacker to take control of the machines - is one of the largest ever found on the internet. Discovered at the end of 2008, Conficker exploited a vulnerability present in all Windows versions that existed at the time. Even though Microsoft had released a patch for the vulnerability around the time of the discovery of Conficker, the botnet continued to grow at an alarming rate.
A consortium of parties including Microsoft and ICANN established the Conficker Working Group (CWG) to fight the botnet. When Conficker was used to sell fake anti-virus software in 2009 for between $50 – 100 duping nearly a million computer users, Law Enforcement joined the fray. The CWG eventually neutralized the botnet by cutting off communications between the operators and the zombie machines forcing the botherders to abandon their botnet. In 2011 several arrests in different countries were made in response to the fake anti-virus scheme.
Healthy global network
But even though the victim machines are no longer part of a zombie army, nearly a million of them remain infected. In June 2014 Conficker was still listed as the 6th largest known botnet. Leaving so many computers vulnerable is detrimental to the overall health of the internet.
Infected computers can be “a magnet for other threats”, write Asghari and colleagues in their paper. “The recent sinkholing attempt of [the botnet] GameoverZeus, for example, is more a tug of war between attackers and defenders, rather than definitive takedown action. The bots that remain after a takedown of C&C [command-and-control] infrastructure may also attract other attackers, as these machines remain vulnerable and hence can be re-compromised.”
With the aim to facilitate better large-scale cleanup efforts of infected computers in the future, the Delft team examined which factors contributed to fighting the Conficker plague. They took a dataset that logs Conficker bots on a daily basis, and looked at how quick the malware spread, the infection levels at peak, and the cleanup rate. They sorted it by country to differentiate between factors like the existence of anti-botnet initiatives, broadband access, piracy rates and the ICT development index.

Source: Post-Mortem of a Zombie: Conficker Cleanup After Six Years
National anti-botnet centers
An increasing number of countries are setting up national anti-botnet centers. These are often public-private partnerships with a central role for Internet Service Providers because of their proximity to end users. These centers are considered a best practice but little research has been done to quantify their success rate.
To their own surprise, Asghari and colleagues found no correlation between the existence of such a national center and the spread or demise of Conficker. “It is somewhat surprising, and disappointing, to see no evidence for the impact of the leading remediation efforts on bot cleanup”, they write.
Piracy and proficiency
The team did find two other factors that have a significant impact on both the growth rate and the cleanup rate. In countries with a high level of pirated copies of the Microsoft operating systems, the malware spread more easily. This outcome they find far less surprising: “In addition to the fact that pirated software might include malware itself, users running pirated OS’s often turn off automatic updates, for fear of updates disabling their unlicensed software — even though Microsoft consistently states that it will also ship security updates to unlicensed versions of Windows.”
The other factor is the ICT development index. This internationally established benchmark indicates ICT maturity based on parameters such as digital infrastructure and literacy. Countries that score high on the index were better equipped to keep Conficker at bay.
For the good of all
This is not so surprising when making the analogy with public health. High quality health care infrastructure and knowledge of and access to nutritious food results in a more healthy population. And just like humanity would be better off if all people could enjoy these benefits, so it is for computers:
“The fact that peak infection levels strongly correlate with ICT development and software piracy, suggests that botnet mitigation can go hand in hand with economic development and capacity building. Helping countries develop their ICT capabilities can lower the global impact of infections over the long run”, Asghari, Ciere and Van Eeten conclude.
Image: Norse: Real-time global cyberattacks map
Read full article
Hide full article


Discussion (0 comments)