On-Chip Trojans
on
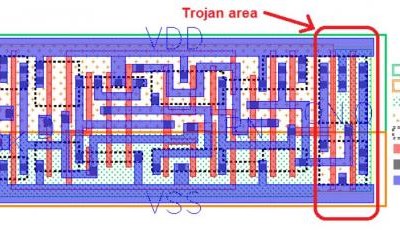
In a recent research paper titled ‘Stealthy Dopant-level Hardware Trojans’ a research team from the US, The Netherlands, Switzerland and Germany showed how a complex integrated circuit could be maliciously compromised.
The changes they made to the chip’s fabrication process did not involve changes to any interconnect masks which would be easily detected by optical inspection. Instead they made changes to the dopant-level to some parts of the chip to alter the semiconductor characteristics. The modifications went undetected by the standard inspection process.
As proof of concept they were able to make changes to several hundred gates of an Intel Ivy Bridge processor which sabotaged the Random Number Generator (RNG) instructions. The exploit works by reducing the amount of entropy the RNG normally uses, from 128 bits to 32 bits. Any cryptographic keys generated by the compromised chip would be easy to crack. The hacked RNG was not detected by any of the "Built-In Self-Tests" mandated by the National Institute of Standards and Technology.


Discussion (0 comments)