Smartphone Security Flaw (again)
on
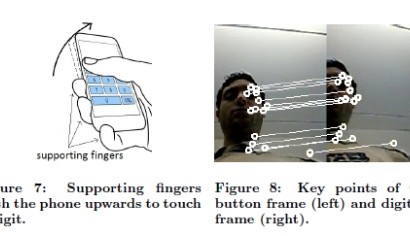
In a report by theUniversityofCaliforniain 2011 researchers developed the TouchLogger malware App to show that information from a phone’s accelerometer and gyro could be used to determine which softkey was being pressed on the screen.
A new report by researchers Ross Anderson and Laurent Simon atCambridgeUniversityreveals a similar flaw but uses information from the phone’s microphone and camera. The microphone is used to identify screen key press events and images from the phones camera are analysed to work out the direction of the phone’s movement and hence the area of the screen that was pressed to produce the movement. This piece of malware is called PIN Skimmer and in a test of 50 4-digit PINs, PIN Skimmer correctly inferred more than 30% of PINs after 2 attempts and more than 50% of PINs after 5 attempts on android-powered Nexus S and Galaxy S3 phones.
Ross Anderson said “Our work shows it’s not enough for your electronic wallet software to grab hold of the screen, the accelerometers and the gyro; you’d better lock down the video camera, and the still camera too while you’re at it. (Our attack can use the still camera in burst mode)”.


Discussion (0 comments)