Certificate Authority System Insecure, Firefox Add-on Offers Alternative
September 05, 2011
on
on
A hack of the Certificate Authority (CA) DigiNotar has moved web browser providers to invalidate all its certificates. Including those authenticating Dutch government web sites. The failing CA system reinforces the call for alternative authentication methods. Here is one in the form of a Firefox add-on.
The breach
The Dutch company DigiNotar discovered its systems were compromised on the 19th of July. However, it chose not to communicate the breach to its partners. Only when Google discovered a false certificate on August 29 there was a first warning that something was amiss. Google informed its fellow browser providers Mozilla Firefox and Microsoft.
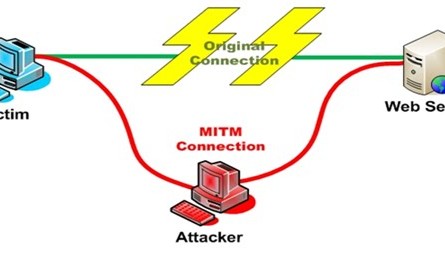
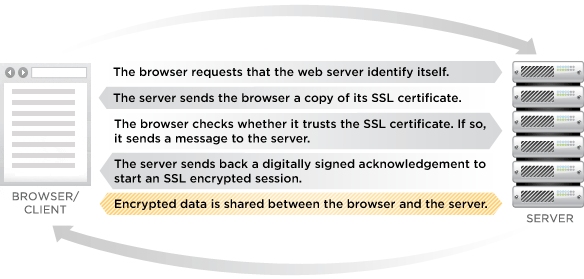
The false certificate was being used for a Man In The Middle (MITM) attack on Google users in Iran. An attacker positioned himself between the user and the Google server. Using the rogue certificate to falsely identify himself to the web browser as a genuine Google server he was able to intercept the data stream between the two points of communication. SSL certificates were called into life in 1995 specifically to prevent these kinds of attacks. Upon initiation of a secure session the web browser requests a copy of a certificate of the server. The copy is checked against a list of trusted certificates to authenticate the server.
Gervase Markham of Firefox published a revealing article detailing the course of events. The attackers finding their way into DigiNotar’s systems stole certificate profiles with which they could issue false certificates. Next to the counterfeit Google certificate another 247 have been identified. But there is no way of telling how many more are in the wild because DigiNotar has been unable to determine how many certificates have been misissued. Nor can they provide the serial numbers which is necessary to revoke them.
In order to guarantee the secure surfing of their users Firefox, Chrome and Explorer decided to terminate the trust in DigiNotar as a CA, rendering all its certificates void. Markham lists a total of 9 serious errors on the side of DigiNotar, which led to this decision. Such as the company’s failure to notify concerned parties of the breach. Whom, forewarned, possibly would have been able to detect the false certificates sooner.
As a result all clients of DigiNotar -who paid the company $1200 on average for the certificates- now have their sites marked as insecure. Firefox in coordination with Bits of Freedom, a Dutch digital rights NGO, crowdsourced a list of affected sites to warn their owners.
Poor government response
DigiNotar’s most notable client is the Dutch Government. The company played a role in PKIoverheid (Public Key Infrastructure government), issuing certificates for privacy sensitive government websites. Such as the general citizen identification site DigiD, which at its launch was promoted by the government as the one-stop shop for all citizen-government interaction. Piet Hein Donner, the Dutch interior minister issued a statement on Saturday morning saying that “users of government sites do no longer have the guarantee they are actually on a government site”.
Bits of Freedom responded on their website saying that citizens have possibly been exposed to data theft since July 19th –the date DigiNotar discovered the hack. Adding to their long standing feud with the government whom they accuse of pushing a digital infrastructure trafficking personal data without paying proper attention to security.
In this case too, the interior minister seems to have dropped the ball. Markham relates that when Firefox decided to annul DigiNotar’s certificates it included those of PKIoverheid. However, Dutch officials then turned to Firefox asking to exempt their certificates from cancellation. An assessment by the Dutch GovCERT (Government Computer Emergency Response Team), had led them to conclude that these had not been compromised, they said. Firefox agreed to comply with the Dutch request until an audit by third party company Fox-IT revealed there was no ground for the GovCERT’s conclusion. The interior minister then had to retract his earlier assurances and Firefox proceeded in removing PKIoverheid certificates from their trusted list.
CA system insecure, a Firefox add-on offers alternative
The issuing of false certificates feeds the growing doubt about the maintainability of the authentication system. Moxie Marlinspike, an outspoken CA skeptic, mapped out the problems in a briefing given on the Black Hat information security conference in August . The system of authenticating web sites is long due to be replaced, says Marlinspike. It was developed in a time when the internet was still so small that everybody practically knew each other and there were 20 sites tops that actually needed securing. The idea of CAs certifying web sites was a workable concept back then. But anno 2011 it has spun out of control.
There are now over 650 CAs. A myriad of companies and organizations across the globe which can sign certificates. It is difficult for browser providers, let alone users, to verify the trustworthiness of these vendors of trust. One failing CA can jeopardize the entire system. An argument that can now be captured in a single word: DigiNotar.
Moreover, there is no opting out. If someone does not trust a CA there is no alternative method to authenticate a web site. A flaw also exposed in this debacle. Clients of the failed CA can’t have their websites authenticated until they sign up with another CA. And they can only hope the new one has better cyber ethics. Equally, users can’t decide to refuse certificates issued by a particular CA because it would mean shutting themselves out of the sites certified by it. And if you don’t trust any CA, like Marlinspike, it means locking yourself out of all secured sites.
So Marlinspike decided to create an alternative for the CA system. He engineered an authentication system called Convergence. It’s an Firefox add-on which he launched on the Black Hat stage. It is based on the idea of multi-path probing aka network perspectives. That is to say, when a browser contacts a website it receives a certificate with which the website identifies itself. In the CA system, the browser than asks an authority to check if it sees the same certificate. If the certificates match, the connection proceeds. This is a form of network perspectives, validating a site by looking at it from different perspectives.
[Edit: In a reaction to this post Gervase Markham points out that this description of the CA system is not quite correct. He writes: "In the CA system, the browser checks to see if the certificate was issued by (signed by) a CA it trusts, and has not been revoked. It does not work as similarly to the Perspectives/Convergence system as you suggest." Thanks Gervase for pointing this out.]
What Convergence does is replacing the CA as a different-perspective-agent with other agents called notaries.
What Convergence does is replacing authentication through certification. Instead it probes the site from different perspectives through agents called notaries. These notaries can be situated anywhere in the web and run by anyone. The difference with CAs is that the user can chose which notaries to use. If for some reason, she no longer trusts the notary, she can block that agent. So contrary to the CA system the user can at any time revoke the trust.
Another difference is the inverted relationship. The authentication initiative no longer lies with the site owner but with the visitor. Instead of the site owner buying a certificate to authenticate her site to third parties, it is now the visitor who initiates the authentication process with the notaries.
For more detailed information about Convergence watch the video below (the part about Convergence starts 35 minutes into the video). Convergence can be downloaded at http://convergence.io.
Moxie Marlinspike’s blog
Image: MITM attack. Source http://4.bp.blogspot.com/
Image: How SSL security works. Source: VeriSign
The breach
The Dutch company DigiNotar discovered its systems were compromised on the 19th of July. However, it chose not to communicate the breach to its partners. Only when Google discovered a false certificate on August 29 there was a first warning that something was amiss. Google informed its fellow browser providers Mozilla Firefox and Microsoft.
The false certificate was being used for a Man In The Middle (MITM) attack on Google users in Iran. An attacker positioned himself between the user and the Google server. Using the rogue certificate to falsely identify himself to the web browser as a genuine Google server he was able to intercept the data stream between the two points of communication. SSL certificates were called into life in 1995 specifically to prevent these kinds of attacks. Upon initiation of a secure session the web browser requests a copy of a certificate of the server. The copy is checked against a list of trusted certificates to authenticate the server.

Gervase Markham of Firefox published a revealing article detailing the course of events. The attackers finding their way into DigiNotar’s systems stole certificate profiles with which they could issue false certificates. Next to the counterfeit Google certificate another 247 have been identified. But there is no way of telling how many more are in the wild because DigiNotar has been unable to determine how many certificates have been misissued. Nor can they provide the serial numbers which is necessary to revoke them.
In order to guarantee the secure surfing of their users Firefox, Chrome and Explorer decided to terminate the trust in DigiNotar as a CA, rendering all its certificates void. Markham lists a total of 9 serious errors on the side of DigiNotar, which led to this decision. Such as the company’s failure to notify concerned parties of the breach. Whom, forewarned, possibly would have been able to detect the false certificates sooner.
As a result all clients of DigiNotar -who paid the company $1200 on average for the certificates- now have their sites marked as insecure. Firefox in coordination with Bits of Freedom, a Dutch digital rights NGO, crowdsourced a list of affected sites to warn their owners.
Poor government response
DigiNotar’s most notable client is the Dutch Government. The company played a role in PKIoverheid (Public Key Infrastructure government), issuing certificates for privacy sensitive government websites. Such as the general citizen identification site DigiD, which at its launch was promoted by the government as the one-stop shop for all citizen-government interaction. Piet Hein Donner, the Dutch interior minister issued a statement on Saturday morning saying that “users of government sites do no longer have the guarantee they are actually on a government site”.
Bits of Freedom responded on their website saying that citizens have possibly been exposed to data theft since July 19th –the date DigiNotar discovered the hack. Adding to their long standing feud with the government whom they accuse of pushing a digital infrastructure trafficking personal data without paying proper attention to security.
In this case too, the interior minister seems to have dropped the ball. Markham relates that when Firefox decided to annul DigiNotar’s certificates it included those of PKIoverheid. However, Dutch officials then turned to Firefox asking to exempt their certificates from cancellation. An assessment by the Dutch GovCERT (Government Computer Emergency Response Team), had led them to conclude that these had not been compromised, they said. Firefox agreed to comply with the Dutch request until an audit by third party company Fox-IT revealed there was no ground for the GovCERT’s conclusion. The interior minister then had to retract his earlier assurances and Firefox proceeded in removing PKIoverheid certificates from their trusted list.
CA system insecure, a Firefox add-on offers alternative
The issuing of false certificates feeds the growing doubt about the maintainability of the authentication system. Moxie Marlinspike, an outspoken CA skeptic, mapped out the problems in a briefing given on the Black Hat information security conference in August . The system of authenticating web sites is long due to be replaced, says Marlinspike. It was developed in a time when the internet was still so small that everybody practically knew each other and there were 20 sites tops that actually needed securing. The idea of CAs certifying web sites was a workable concept back then. But anno 2011 it has spun out of control.
There are now over 650 CAs. A myriad of companies and organizations across the globe which can sign certificates. It is difficult for browser providers, let alone users, to verify the trustworthiness of these vendors of trust. One failing CA can jeopardize the entire system. An argument that can now be captured in a single word: DigiNotar.
Moreover, there is no opting out. If someone does not trust a CA there is no alternative method to authenticate a web site. A flaw also exposed in this debacle. Clients of the failed CA can’t have their websites authenticated until they sign up with another CA. And they can only hope the new one has better cyber ethics. Equally, users can’t decide to refuse certificates issued by a particular CA because it would mean shutting themselves out of the sites certified by it. And if you don’t trust any CA, like Marlinspike, it means locking yourself out of all secured sites.
So Marlinspike decided to create an alternative for the CA system. He engineered an authentication system called Convergence. It’s an Firefox add-on which he launched on the Black Hat stage. It is based on the idea of multi-path probing aka network perspectives. That is to say, when a browser contacts a website it receives a certificate with which the website identifies itself. In the CA system, the browser than asks an authority to check if it sees the same certificate. If the certificates match, the connection proceeds. This is a form of network perspectives, validating a site by looking at it from different perspectives.
[Edit: In a reaction to this post Gervase Markham points out that this description of the CA system is not quite correct. He writes: "In the CA system, the browser checks to see if the certificate was issued by (signed by) a CA it trusts, and has not been revoked. It does not work as similarly to the Perspectives/Convergence system as you suggest." Thanks Gervase for pointing this out.]
What Convergence does is replacing authentication through certification. Instead it probes the site from different perspectives through agents called notaries. These notaries can be situated anywhere in the web and run by anyone. The difference with CAs is that the user can chose which notaries to use. If for some reason, she no longer trusts the notary, she can block that agent. So contrary to the CA system the user can at any time revoke the trust.
Another difference is the inverted relationship. The authentication initiative no longer lies with the site owner but with the visitor. Instead of the site owner buying a certificate to authenticate her site to third parties, it is now the visitor who initiates the authentication process with the notaries.
For more detailed information about Convergence watch the video below (the part about Convergence starts 35 minutes into the video). Convergence can be downloaded at http://convergence.io.
Moxie Marlinspike’s blog
Image: MITM attack. Source http://4.bp.blogspot.com/
Image: How SSL security works. Source: VeriSign
Read full article
Hide full article


Discussion (0 comments)