Is a Ban on Social Media Technologically Possible?
August 16, 2011
on
on
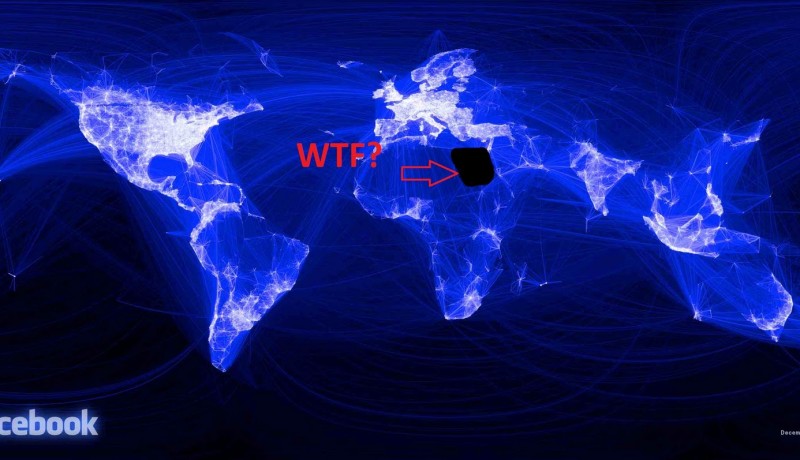
In the wake of the London riots Prime Minister David Cameron floated the idea of a partial ban on social media. But is the technology in place to block a specific person from a specific service? And if so, how difficult is it to elude such a ban.
In his first address to Parliament since riots spread through London and other major cities, Cameron said: “Free flow of information can be used for good. But it can also be used for ill. And when people are using social media for violence we need to stop them. So we are working with the Police, the intelligence services and industry to look at whether it would be right to stop people communicating via these websites and services when we know they are plotting violence, disorder and criminality.”
Free speech advocates immediately reacted saying that a social media shut down would be a violation of the right to freedom of expression as laid down in article 19 of the Universal Declaration of Human Rights: “Everyone has the right to freedom of opinion and expression; this right includes freedom to hold opinions without interference and to seek, receive and impart information and ideas through any media and regardless of frontiers”.
But besides questions concerning the legitimacy of Cameron’s proposal, there is also the question whether a social media clampdown is technologically feasible.
The most direct way to ban a user from a social network is to block his or her user account. Technologically that is a simple action for a network administrator. But a person can nimbly parry such a ban by setting up a new user account. Also, this method is easily available to the social networks but not to the government. It would need full cooperation of the social network in question to execute the ban.
A more effective way for an administrator to block a user is IP banning. Blocking the IP address of a computer terminates the connection between the computer and the site. However, the disadvantage of IP banning is that it is difficult to block one specific user. Many ISP’s allocate IP addresses dynamically. This means the targeted computer shares a range of IP addresses with a bunch of other devices thrown together by the ISP. Taking out the targeted computer will terminate the connection of its unwitting neighbors too.
But an IP ban isn’t water tight either. It can be skirted by sending data via an anonymizing proxy server which strips the user’s data package from identifiable data before sending it along to the destination server. Another way to mask an IP address is using a Virtual Private Network (VPN). A VPN uses security procedures and tunneling protocols to channel data privately over a public network.
Another difficulty lies in pinpointing the accounts of those users who are “plotting violence, disorder and criminality”. Social platforms produce a data firehose. To mine that data for actual threats of violence is a monumental task. An algorithm can filter out only so much. It can flag messages based on keywords but it can’t interpret context like a human can. Undoubtedly certain parameters can narrow things down a bit. But in the end humans would have to check every message left in the dragnet because an algorithm can’t tell the difference between a joke and a genuine threat.
In its quest to find the culprits the British government can decide to go drastically totalitarian, follow in the footsteps of China and Saudi Arabia, build a national firewall and inspect all internet traffic. The Saudi’s built one gigantic proxy server through which all the country’s data packages are routed, inspected and censored. Despite the fact that the Saudi government is exceptionally well-equipped for a full scale censorship (for instance, the entire telecommunications infrastructure is government-owned) Saudi’s still find ways to penetrate the firewall. They make international calls to connect to uncensored foreign ISP’s, they employ VPN or set up satellite dishes for internet access. [Information on Saudi Arabia from Kenneth Geers, see below]
The last resort for the British government would be to go for a local internet shut down. But the Egyptian uprising last January proved the resilience of the signal even during a government enforced nation wide black out. Although communications were severely slowed down they couldn’t be completely stopped. France Data Network and Telecomix News Agency provided a dial-up internet access for Egyptians. And Google rapidly set up a service that let people phone in their tweets.
It appears that even if Cameron can persuade Parliament to go for a clampdown in social media it’s going to be very difficult to make it technologically possible. As Electric Frontier Foundation co-founder John Gilmore famously said: “The Internet interprets censorship as damage and routes around it.”
Cyber security expert Kenneth Geers wrote an interesting book Strategic Cyber Security which he offers as a free download here.
Photo: First-news.blogspot.com
In his first address to Parliament since riots spread through London and other major cities, Cameron said: “Free flow of information can be used for good. But it can also be used for ill. And when people are using social media for violence we need to stop them. So we are working with the Police, the intelligence services and industry to look at whether it would be right to stop people communicating via these websites and services when we know they are plotting violence, disorder and criminality.”
Free speech advocates immediately reacted saying that a social media shut down would be a violation of the right to freedom of expression as laid down in article 19 of the Universal Declaration of Human Rights: “Everyone has the right to freedom of opinion and expression; this right includes freedom to hold opinions without interference and to seek, receive and impart information and ideas through any media and regardless of frontiers”.
But besides questions concerning the legitimacy of Cameron’s proposal, there is also the question whether a social media clampdown is technologically feasible.
The most direct way to ban a user from a social network is to block his or her user account. Technologically that is a simple action for a network administrator. But a person can nimbly parry such a ban by setting up a new user account. Also, this method is easily available to the social networks but not to the government. It would need full cooperation of the social network in question to execute the ban.
A more effective way for an administrator to block a user is IP banning. Blocking the IP address of a computer terminates the connection between the computer and the site. However, the disadvantage of IP banning is that it is difficult to block one specific user. Many ISP’s allocate IP addresses dynamically. This means the targeted computer shares a range of IP addresses with a bunch of other devices thrown together by the ISP. Taking out the targeted computer will terminate the connection of its unwitting neighbors too.
But an IP ban isn’t water tight either. It can be skirted by sending data via an anonymizing proxy server which strips the user’s data package from identifiable data before sending it along to the destination server. Another way to mask an IP address is using a Virtual Private Network (VPN). A VPN uses security procedures and tunneling protocols to channel data privately over a public network.
Another difficulty lies in pinpointing the accounts of those users who are “plotting violence, disorder and criminality”. Social platforms produce a data firehose. To mine that data for actual threats of violence is a monumental task. An algorithm can filter out only so much. It can flag messages based on keywords but it can’t interpret context like a human can. Undoubtedly certain parameters can narrow things down a bit. But in the end humans would have to check every message left in the dragnet because an algorithm can’t tell the difference between a joke and a genuine threat.
In its quest to find the culprits the British government can decide to go drastically totalitarian, follow in the footsteps of China and Saudi Arabia, build a national firewall and inspect all internet traffic. The Saudi’s built one gigantic proxy server through which all the country’s data packages are routed, inspected and censored. Despite the fact that the Saudi government is exceptionally well-equipped for a full scale censorship (for instance, the entire telecommunications infrastructure is government-owned) Saudi’s still find ways to penetrate the firewall. They make international calls to connect to uncensored foreign ISP’s, they employ VPN or set up satellite dishes for internet access. [Information on Saudi Arabia from Kenneth Geers, see below]
The last resort for the British government would be to go for a local internet shut down. But the Egyptian uprising last January proved the resilience of the signal even during a government enforced nation wide black out. Although communications were severely slowed down they couldn’t be completely stopped. France Data Network and Telecomix News Agency provided a dial-up internet access for Egyptians. And Google rapidly set up a service that let people phone in their tweets.
It appears that even if Cameron can persuade Parliament to go for a clampdown in social media it’s going to be very difficult to make it technologically possible. As Electric Frontier Foundation co-founder John Gilmore famously said: “The Internet interprets censorship as damage and routes around it.”
Cyber security expert Kenneth Geers wrote an interesting book Strategic Cyber Security which he offers as a free download here.
Photo: First-news.blogspot.com
Read full article
Hide full article


Discussion (0 comments)