Staggering Number of Industrial Control Systems Exposed to the Internet
October 23, 2014
on
on
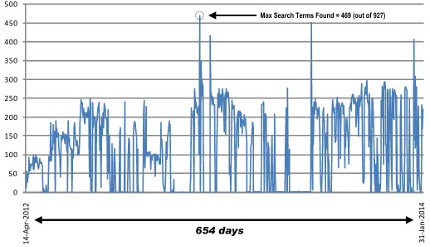
Researchers from the cyber security firm Infracritical ran a two year search for industrial control systems directly connected to the Internet. They found millions of systems exposed, endangering the security of critical infrastructure.
Infracritical co-founder Bob Radvanovsky and colleague Jacob Brodsky knew from their work in infrastructure security that many critical systems are exposed to the internet. They just had no idea about the scope, were we talking tens of thousands? Hundreds of thousands? And so they started project SHINE to probe the internet for SCADA (supervisory control and data acquisition) systems and industrial control systems.
SHINE
SHINE stands for Shodan Intelligence Extraction. Shodan is a search engine to find specific devices connected to the internet. Just like Google bots are crawling the web to index information, Shodan bots scan for connected devices on the internet.
2.2 million systems
The Infracritical team formulated sets of search queries to identify control systems typically used in critical infrastructure like water treatment, electricity, health care, transportation, and financial transactions. The queries consisted of names of manufacturers like Siemens and EnergyICT often supplemented with identifying names or numbers of specific devices.
In the 654 days that project SHINE was operational it found 2.2 million devices matching the search queries publicly available on the internet. When Radvanovsky and Brodsky terminated the project in January 2014 they still were getting responses. The 2,2 million isn't the exhaustive number of exposed systems, its just the yield of 11 months of querying.
Security threat
The metadata Shodan provides can be extensive and can include the location of the device, country of origin and the IP-address which can be used to do a reverse lookup to find out the device owner. Shodan can also reveal the protocol type (HTTP, SNMP, Telnet, etc.) and the firmware running the device. The Infracritical team warns that the information can be used to mount an attack. Knowledge about firmware, for instance, enables an attacker focus on known vulnerabilities.
Top 21 countries
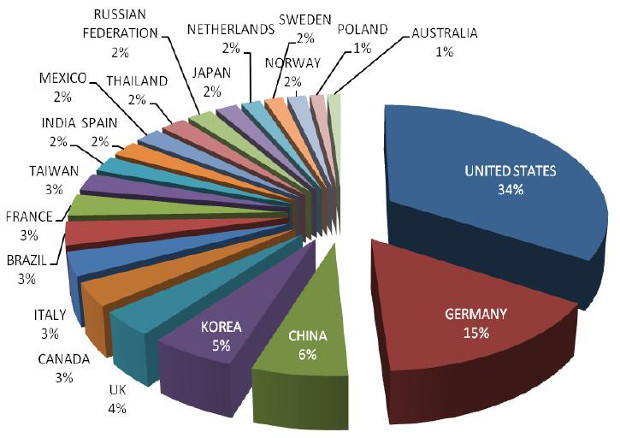
SHINE found 84% of its total collection of vulnerable systems in 21 countries.
Awareness
The stated purpose of the SHINE project is to create awareness for the lack of security in critical infrastructure. Radvanovsky and Brodsky took a closer look at some of the samples and found out that “most exposures appear to be accidental. In other words, it is the result of poorly configured network infrastructure. The asset owners may not realize the problem until perhaps someday someone takes the time to locate the asset owners to advise them that their infrastructure is exposed. Of course, it is also entirely possible that someone with ill intentions will find such assets first.”
Focus on security
They call on the industry to pay more attention to security, ask asset owners to pay better attention during installation and get beyond the default settings and implore governments to improve regulations. Radvanovsky and Brodsky found that vulnerable systems often actually complied to regulations: “The industry must get past this terrible practice of compliance-based security and focus instead on an attitude of safety, vigilance, and perfomance awareness”.
The researchers made the findings of project SHINE publicly available.
Images: Project SHINE findings report
Infracritical co-founder Bob Radvanovsky and colleague Jacob Brodsky knew from their work in infrastructure security that many critical systems are exposed to the internet. They just had no idea about the scope, were we talking tens of thousands? Hundreds of thousands? And so they started project SHINE to probe the internet for SCADA (supervisory control and data acquisition) systems and industrial control systems.
SHINE
SHINE stands for Shodan Intelligence Extraction. Shodan is a search engine to find specific devices connected to the internet. Just like Google bots are crawling the web to index information, Shodan bots scan for connected devices on the internet.
2.2 million systems
The Infracritical team formulated sets of search queries to identify control systems typically used in critical infrastructure like water treatment, electricity, health care, transportation, and financial transactions. The queries consisted of names of manufacturers like Siemens and EnergyICT often supplemented with identifying names or numbers of specific devices.
In the 654 days that project SHINE was operational it found 2.2 million devices matching the search queries publicly available on the internet. When Radvanovsky and Brodsky terminated the project in January 2014 they still were getting responses. The 2,2 million isn't the exhaustive number of exposed systems, its just the yield of 11 months of querying.
Security threat
The metadata Shodan provides can be extensive and can include the location of the device, country of origin and the IP-address which can be used to do a reverse lookup to find out the device owner. Shodan can also reveal the protocol type (HTTP, SNMP, Telnet, etc.) and the firmware running the device. The Infracritical team warns that the information can be used to mount an attack. Knowledge about firmware, for instance, enables an attacker focus on known vulnerabilities.
Top 21 countries
SHINE found 84% of its total collection of vulnerable systems in 21 countries.

Awareness
The stated purpose of the SHINE project is to create awareness for the lack of security in critical infrastructure. Radvanovsky and Brodsky took a closer look at some of the samples and found out that “most exposures appear to be accidental. In other words, it is the result of poorly configured network infrastructure. The asset owners may not realize the problem until perhaps someday someone takes the time to locate the asset owners to advise them that their infrastructure is exposed. Of course, it is also entirely possible that someone with ill intentions will find such assets first.”
Focus on security
They call on the industry to pay more attention to security, ask asset owners to pay better attention during installation and get beyond the default settings and implore governments to improve regulations. Radvanovsky and Brodsky found that vulnerable systems often actually complied to regulations: “The industry must get past this terrible practice of compliance-based security and focus instead on an attitude of safety, vigilance, and perfomance awareness”.
The researchers made the findings of project SHINE publicly available.
Images: Project SHINE findings report
Read full article
Hide full article


Discussion (0 comments)