| Modern cars are packed from front to back with 'clever' chips; the software that is stored in them provides a large part of the functionalit...
More about Cyber Security (34)
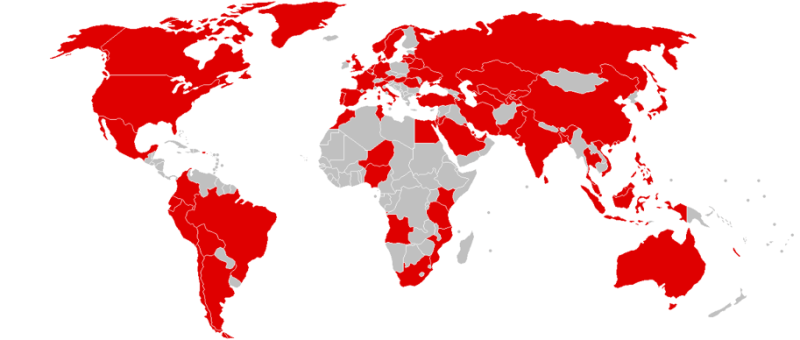
| The cyberattack that hit the world on Friday May 12th is a stark reminder that governments need to rethink cybersecurity policies. The chaos...
| With the emergence of the Internet of Things an increasing number of actuators and sensors are connected to the global network. The internet...
| With an expected 500 billion connected devices in 2022, we can't secure the Internet of Things on the device level, said Professor Frank Fit...
| Are your communications secure? There are many overhyped "cryptophones" and crypto software programs available today, but can you really tru...
| What better than a little scare to start the week? Here is one that will not only make connected business men and bankers raise an eyebrow,...
| By 2020 the security of the internet will be so abysmal, that anyone who goes online must assume their systems and data are already compromi...
| With nearly a billion people signed on, India has the largest biometric identity system in the world. The Aadhaar identity system requires c...
| The security of the internet remains rickety and now we're starting to hook up physical objects like cars, smart meters and home automation...
| In 2013 the Guardian was ordered to destroy laptops containing the Snowden documents under supervision of GCHQ. The British secret service i...