What Is RISC-V?
on

To start, it is essential to understand that RISC-V is an Instruction Set Architecture, or ISA [1], and not a processor. This means that the community behind RISC-V has put together a description of how a processor design should work, should you choose to base it on their RISC-V ISA. And when we say "design," we really do mean creating the processor with all its registers, accumulators, math operations, memory buses, and everything else.
The ISA documents the supported operations, the memory addressing capabilities, how the stack functions, and what happens when interrupts occur, to name just a few items. With regard to supported operations, it explains how many bits are used to encode the instruction and which bits are used to encode the source of any operands needed.
The reason for the excitement is that the ISA is free and open. Open means that anyone can contribute to its development, while free means that it doesn’t cost a bean to use. However, just like Arduino board designs are open and free to use, that doesn’t mean that it doesn’t cost money to acquire a board, and the same applies to building your dream RISC-V-based design.
What Is RISC-V Competing Against?
Every processor has an ISA; almost all are proprietary, and some are licensable. Microchip produces devices that use 8-bit and 16-bit PIC processors and, somewhere, there is an ISA to describe them. These are proprietary cores that belong to and are sold by Microchip in their microcontrollers. If you want to build your own microcontroller, you’ll probably take a look at Arm and MIPS. These proprietary cores are licensable as intellectual property (IP). The businesses behind them do all the work to convert the ISA into a good processor design, develop tools to support them, create other related infrastructure, and charge a fee for you to use them. The challenge that arises is when these options don’t quite do what you want to achieve.
Your new application may need to perform one task, say encryption, really fast but with minimal power draw. A potential licensable processor IP may execute your task in 100 instructions. If you now wish to reduce power consumption, you’ll need to find a silicon fabrication facility (fab) specializing in low-power. That may be more expensive than a ‘general-purpose’ fab process, resulting in your incredible product being too expensive for your target market.
However, you may also have some clever engineers who could optimize your code’s execution time by creating new instructions for the processor but, because the ISA is proprietary, you’re not allowed to modify it. So, you’re stuck with a processor performance problem that you need to solve with a manufacturing approach. More on this later.
What Does It Do Out-of-the-Box?
The short answer is “not much but enough.” Basically, you need to start by choosing the precise architecture you want. Currently, there are 32-bit and 64-bit ISAs defined, with a 128-bit ISA being worked on too. These base definitions are named RV32I and RV64I. If you select the RV32I, you’ll have 49 instructions [2] at your disposal. The "I," incidentally, stands for "Integer." Included are all the basic integer arithmetic and logic instructions (ADD, SUB, AND, OR, XOR), shifts, compare, jump and link, and some system instructions [3]. If you’re looking to support compact code, you may be interested in the "C" option. This provides 16-bit instruction encoding, something similar to the Arm Thumb mode. Multiplication and division (M), atomic (A), and floating-point (F, D, and Q) instructions can be added too.
The next step is to design your processor core based upon the specifications of the chosen options in a Hardware Description Language [4] (HDL), such as VHDL or Verilog. As this bit is not easy, this is where the community starts to come in. Designing processors take a lot of skill, so there are a bunch of people and businesses that provide you with ready-to-use designs. If you want to go the "free" route, you should look no further than the PULP Platform [5], created by the ETH Zurich and Università di Bologna. Their CV32E40P RV32IM[F]C implementation is available on GitHub [6], and the instruction decoder is here [7] if you’d like to see how something like this is implemented. Another implementation is the BOOM project, a high performance and parameterizable core for architecture research, developed by the University of California, Berkeley (Figure 1).
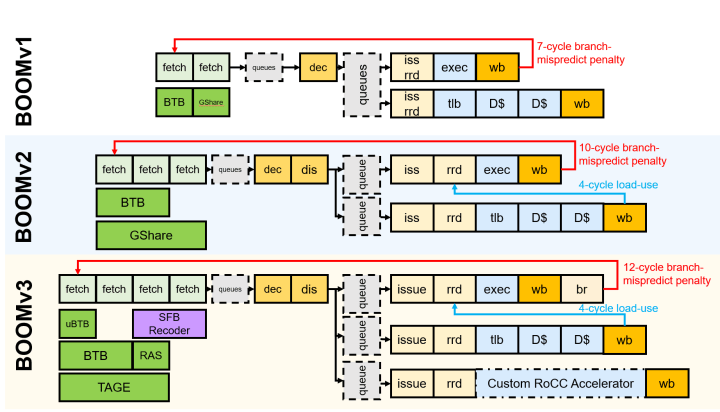
If you’re in a hurry and need some support, then you’ll need to put some money on the table and license an implementation from someone like SiFive [8]. They have a range of 32- and 64-bit designs available [9] that can also be customized.
How Can I Try Out RISC-V?
Despite RISC-V having been around for some time, there is not much silicon available for us to test. In the context of the industry, RISC-V is still relatively new. If you’re into microcontrollers, you will have seen how most of the industry have adopted Arm, moving away from their proprietary cores. That was a strategic, long-term investment. A move now to RISC-V would only save on the royalties paid to Arm and deliver users few benefits. They would also need to get their development teams up-to-speed on RISC-V, integrate it with all their other IP (analog, timers, buses, interfaces, memories), update the development IDE, compiler, debugger, and so on.
If you own a Seagate or Western Digital hard drive, you may already be ‘using’ RISC-V [10] [11]. But you probably actually want to run code on this core, not just own a product that uses it. The fastest way to do this is using a simulator such as emulsiV [12], provided by ESEO, that uses their RISC-V core implementation “Virgule” (Figure 2).
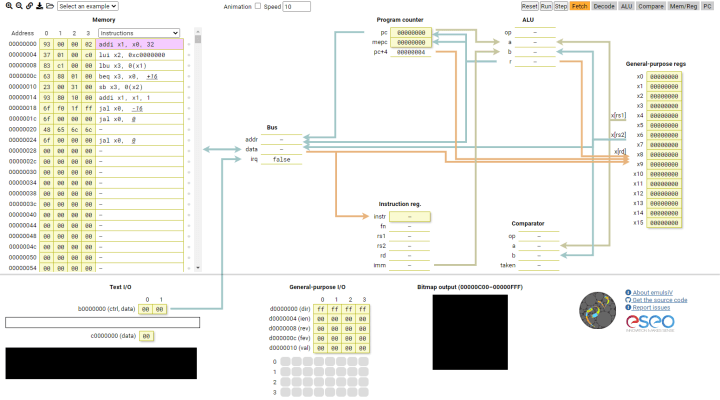
In addition to the processor, the simulator offer some text input/output, a bitmap output, and some general-purpose I/O (GPIO). Seven examples cover the basics, from addition and outputting ASCII text, to control of the GPIOs. A nice touch is the “animation” option (checkbox top middle) that shows where all the data comes from and goes as the code executes. If you like, you can try the code in Listing 1 by copying it into a text editor, saving the file as program.hex, and uploading it into the simulator.
If you’d like to experience RISC-V in Arduino format, the HiFive1 Rev B is currently available through CrowdSupply [13]. It uses the SiFive FE310-G002 microcontroller [14]. This is a bare-bones device with only digital peripherals (I2C, UART, SPI, PWM, GPIO) and some SRAM, relying on an off-chip QSPI flash for non-volatile storage. The board includes a Wi-Fi and Bluetooth module along with a Segger J-Link for USB debugging.
At the other end of the performance spectrum is the Microchip PolarFire SoC [15] that places four 64-bit RISC-V cores alongside an FPGA. This provides a highly-configurable platform that can run Linux while simultaneously supporting hard real-time applications.
How Do I Customize My RISC-V?
Earlier, we mentioned that RISC-V’s practical benefit was that you can tune the instruction set to meet individual application needs. This means that if the processor implementation you’ve found does 95% of what you need, you can go in and add some nifty extra functionality to implement the remaining 5%. Let’s assume that your application makes heavy use of the ChaCha [16] stream cipher [17], as described in an application note [18] from Imperas, another RISC-V player that provides verification, analysis, and profiling tools.
You’ve run your ChaCha implementation on a RISC-V core and noticed that it is eating a significant amount of processing time. Not only do you want to improve the execution time, but you also want to benefit from the drop in power that results due to the reduced execution time, perhaps using it to enter a low-power sleep mode.
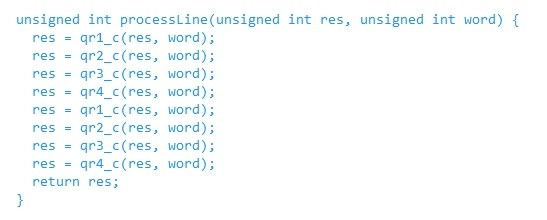
The code (Listing 2) makes extensive use of the XOR and rotate instructions in a step known as ‘quarter rounds’ for which four C qrX_c() functions have been written. A processLine() function calls these four functions to perform encryption. Analysis of execution times shows that the processor spends around 55% of its time on this task, around 32% of which is spread across the four quarter-round functions (Figure 3).
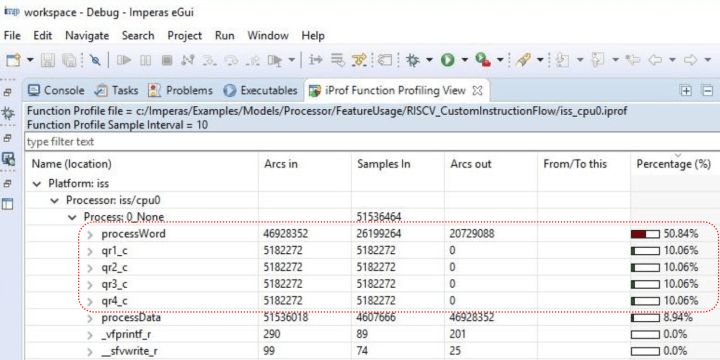
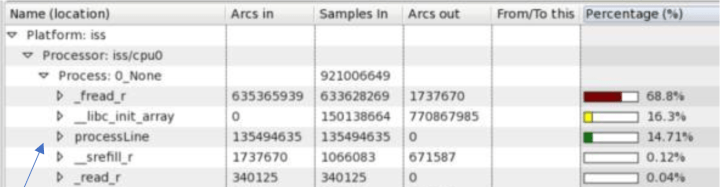
With RISC-V, we can simply implement four dedicated quarter-round instructions that execute in a single cycle instead of relying on the code the C compiler is forced to generate. This is because there is a section reserved in the ISA for customized instructions. Initially, the instructions can be added to a RISC-V design with the instruction’s implementation coded in C. This allows the new instructions to be simulated to test their functionality and checks if a performance improvement is attainable. In this case, with dedicated quarter-round instructions available on the customized RISC-V core, the processLine() function requires less than 15% of the available processor performance (Figure 4). If this is considered a success, the development team can then develop the hardware implementation of the instructions in Verilog.
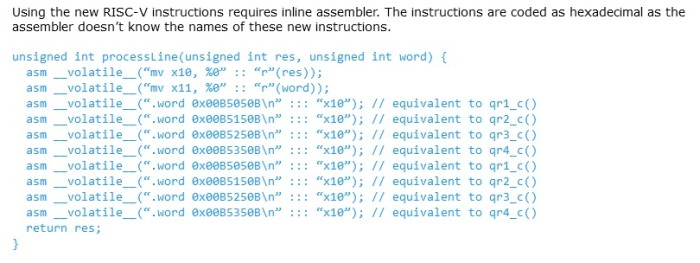
Using the new instructions is, alas, not as easy as recompiling the C code (Listing 3). Modifying a RISC-V compiler to utilize the new instructions is an enormous effort. Instead, the hex-encoded instructions are called using inline assembler in the same manner as hand-optimized code.
How Can I Contribute?
If you’re interested in helping the ongoing development of RISC-V, you’re in luck! RISC-V International [19] is the organization trusted with developing and promoting all things RISC-V (Figure 5). Individuals can join as Community Members [20] or, if you want to build a career on it, there are plenty of businesses and universities [21] who are actively involved.

If you’re expecting a wide array of RISC-V microcontrollers to hit the market, you may be disappointed. GigaDevice offers some devices [22], and there is another from a Russian supplier targeting the smart metering market [23]. However, Arm is too entrenched with the big players, and start-ups will struggle to compete in this saturated market, even with the financial benefit of a processor for which royalties do not need to be paid.
Instead, we are more likely to see RISC-V being used in specialized applications where the ability to customize the core brings huge benefits, such as ultra-low power [24]. With issues around licensing technology to China, RISC-V is proving a popular alternative to acquiring IP from the United States. Alibaba has announced a 16-core, 2 GHz, 64-bit RISC-V built in a 12 nm process [25] and indicates that the core is being viewed for use in server infrastructure. Finally, the European Processor Initiative [26] has been looking at heterogeneous architectures that could see Arm and RISC-V (or other cores) side-by-side. The aim here is to get the best of both worlds by using the best processor for each computing challenge in multicore designs.
RISC-V is not the first free and open attempt at processor IP, but it has been the most successful to date. Given its heritage, flexibility, open approach, interest from academia, and extensive industry support, it is a technology that will accompany a generation or more of engineers for their entire careers.



Discussion (0 comments)