| During these turbulent times, it can be difficult to keep up with all the electronics industry news. Elektor is here to help. This week we u...
More about Hacking (11)
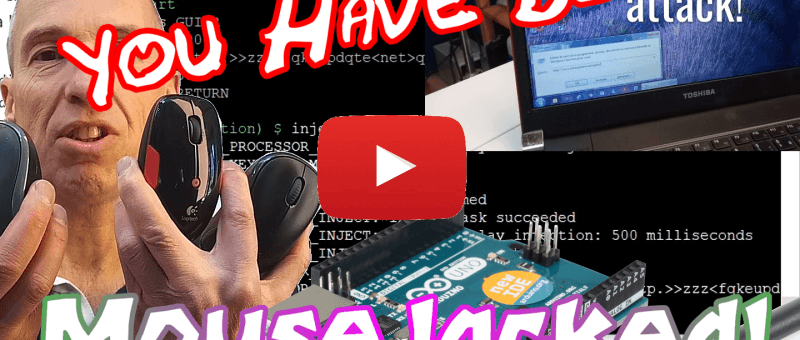
| Wireless mice, especially the older ones, can turn well-protected computers into vulnerable systems. Cheap and readily available tools like...
| Wireless mouses, especially the older ones, can turn well-protected computers into vulnerable systems.
| From calculations made by the University of Twente, it appears that an attack on Bitcoin is easier to carry out than what has generally been...
| The increasingly sophisticated use of automation (with machinery, industrial processes, chemical industry, power generation / distribution a...
| Now available in the Elektor Store is the brand new title: The Car Hacker's Handbook. This book aims to give you a deeper understanding of t...
| Multimeters are nice and useful tools and you probably own at least one. Most of them have a large display to show the value, but no serial...
| Finally, Elektor are bringing you the essential guide of what to do should a Zombie Apocalypse hit. This indispensable guide to survival aft...
| Chaos Communication Congress: Engaging Technology and Its Impact on Society High-level talks about technology as well as reflections on the...
| Unless a geomagnetic storm throws us back into the pre-electronic age, communication networks will play an ever larger role in humanity's de...