Secure Boot Solution for Raspberry Pi
on
The ubiquity and simplicity of the Raspberry Pi have made it very popular and not just with hobbyists. Over the years, and thanks to the introduction of the Raspberry Pi Compute module, it has also found its way into industrial applications. However, equipment based on this approach has suffered from a significant Achilles’ heel: the primary mass-storage solution — namely, SD cards — lack any form of data protection.
The Raspberry Pi itself does not provide any support for a trusted secure boot. Thus, the average user can remove your SD card, make a copy of it, and investigate the files, firmware, and any user data collected. To tackle this, Swissbit developed a solution that encrypts the data inside the SD card and integrates the authentication infrastructure required to offer a secure-boot solution.
Swissbit AG
The company headquarters of Swissbit AG are in Switzerland and, until 2001, it was part of Siemens AG. Specializing in memory and storage products, and with production facilities in Berlin, Germany, they can create and manufacture unique storage solutions using their in-house design capabilities. Their Secure Boot Solution for Raspberry Pi is one such product that has resulted from this unique set of capabilities.
Raspberry Pi and the Missing Security
When working with a Raspberry Pi, you will notice that it uses an implicit chain of trust, which means that, regardless of the boot media used, the Raspberry Pi will try to execute code from it. This opens it up to attacks that can compromise the device’s operating system. Since any user of your device or an attacker has full access to the boot device’s data, you may not even recognize that a system has been copied or modified with malware or data-mining tools. In a worst-case scenario, third-parties could use the device to attack the networks to which the Raspberry Pi is attached.
The addition of a more secure boot solution to a Raspberry Pi is a sensible option to counter this. However, as the hardware itself cannot be changed, a smart solution is required that can be retrofitted to existing deployments. This is where the PS-45u DP “Raspberry Edition” from Swissbit shows its strengths and at a reasonable price point. Being an SD card, it can simply replace your existing storage medium while seamlessly adding secure boot and data protection to your hardware.
Inside an SD Card
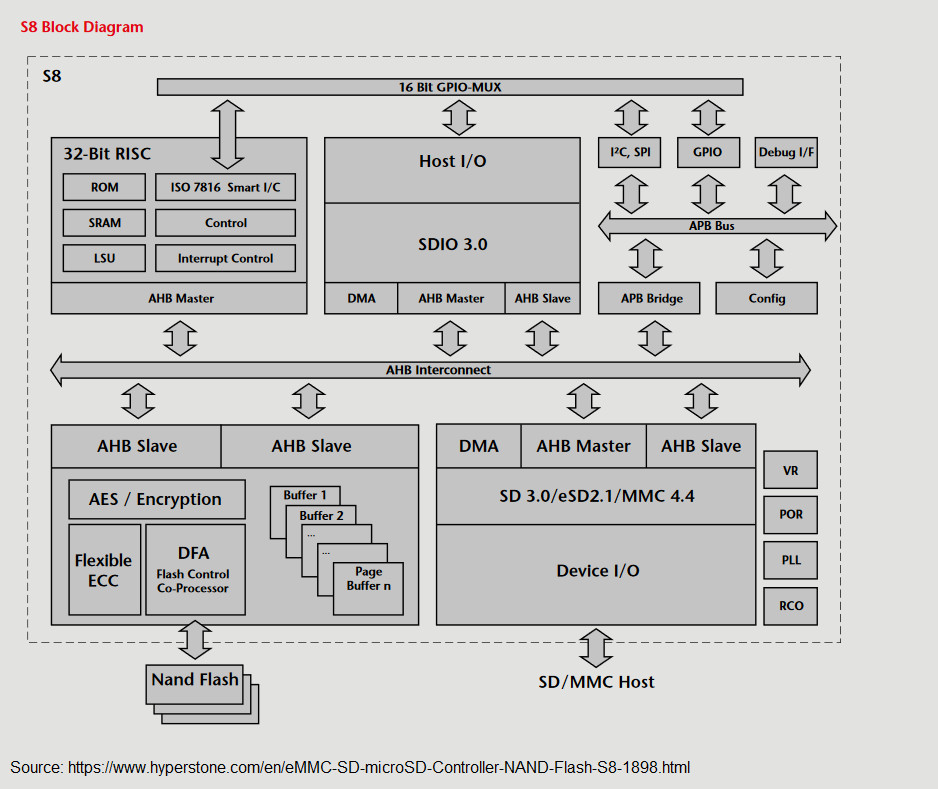
To understand why this solution is unique and why having ownership of memory production facilities comes in handy, we need to start by examining an SD card’s composition. The two crucial components are the NAND flash memory and the memory controller. The memory controller handles the write, erase, and read sequences sent by the host using standardized commands. NAND flash itself, with its increasing density, is not flawless. Somewhere in the memory, there will be some bits that don’t behave as intended. Such faults need to be detected and, if possible, corrected. Additionally, every write and read to a NAND flash wears the bits of the memory out, leading it to fail over time. The memory controller also manages this.
The memory controller acts like a microcontroller (see the example in Figure 1) with a CPU, specialized hardware for handling flash, and the host interface. It lies between your device (the host) and the raw NAND memory hiding the real read and write operations, dealing with bad bits, and handling wear leveling to extend the lifespan of the SD card. The less each data bit is written, the lower the probability that it will fail.
PS-45u DP “Raspberry Edition”
Since Swissbit designs and manufactures their SD cards, their memory controller can be optimized or extended as needed. While consumer SD cards simply present the NAND memory to the host, this new solution has added additional security elements. The PS-45u DP ‘Raspberry Edition’, as shown in Figure 2, is an SD card with security-enhancements that work independently of the host CPU.

More detail on the card’s technical specification can be found in Table 1.

The host, in this case the Raspberry Pi, simply sees an SD card and, if unlocked, can access the data on it. Currently, this “Raspberry Edition” of the PS-45u DP functions with the Raspberry Pi 2 and Raspberry Pi 3B+ models with the authentication implemented in a Swissbit-customized pre-boot phase to unlock access to the SD card data. The card is also hardened to ensure data integrity on loss of power. Those used to operating Raspberry Pi with SD cards will know that some brands get corrupted even during a clean shutdown due to glitches on the power rails and data lines. However, something that no SD card can prevent is an interrupted OS write to the SD card: the best that can be expected is an attempt at recovery when the system is next booted.
The PS-45u DP “Raspberry Edition” is available in 8 GB and 32 GB versions directly from Mouser Electronics. Besides the added robustness, these cards also offer onboard encryption and authentication. For the authentication, there are three methods currently supported that are listed in Table 2. This means that only with the correct access token — a PIN, USB Token, or authentication server — will the data be unlocked and accessible.
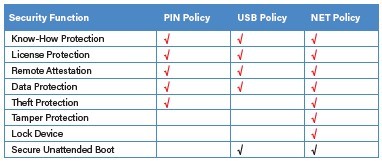
The PIN Policy means that a pre-defined pin must be entered at the command line at bootup. The USB Policy works in conjunction with the PU-50n USB stick (Figure 3) as an authentication token that is also available at Swissbit.

Its technical specification is provided in Table 3.

This is similar to a license dongle that is provided with certain higher-priced PCB design tools. The final option is the NET Policy. This requires the implementation of an authentication server running somewhere on your network that will authenticate or refuse use of the SD card.
To evaluate a system with PIN security you need a Raspberry Pi (Model 3B+ recommended) and a PS-45u DP “Raspberry Edition.” For evaluation of the NET policy in addition to the requirements for the PIN policy, you need a second Raspberry Pi and one regular microSD card (recommended: S-50u).
For evaluation of the USB policy in addition to the requirements of the PIN policy, you will need one USB PU-50n DP “Raspberry Edition”. Figure 4 gives a short overview for the required items to evaluate one of the three policies.

Retrofitting Enhanced Security to Existing Applications
Since the Raspberry Pi requires access to some core firmware files when booting, the PS-45u DP “Raspberry Edition” has been designed with a unique security feature that allows seamless integration with existing projects. If the SD card is secured, the first partition is in a read-only state. This allows the Pi to load the basic firmware and the first part of the software that checks if a valid token is installed. While this first stage firmware can be read by anyone, it stops an attacker from gaining access to the remainder of the SD card. This protects your software installation from unauthorized accesses using one of three potential authentication methods as follows.
PIN Policy
Using the SD card with the PIN Policy is the simplest approach for added security measures. The SD card needs to be configured according to the Swissbit SecureBoot SDK RPi User Manual. Currently, Windows is required to set the SD card up (see Figure 5). The tools included allow a PIN for the card to be set but the use of the standard ASCII character set is highly recommended. Even if you can lock and unlock your card in Windows with the special characters on your keyboard, it should be noted that the Raspberry Pi forces the use of a UK (qwerty) keyboard layout during boot. This may cause irritation when using non-UK keyboards and alphanumeric PINs. For example, when a PIN “qwertz” has been set in the Windows tool and the Raspberry Pi is booting with a German keyboard connected, you will have to enter “qwerty” (since “y” and “z” are switched in German keyboard layout compared to UK layout) to successfully authenticate.

Besides the challenges provided by the keyboard layout, this approach also means that the PIN must be entered every time upon booting to unlock the SD card and continue with the remaining boot process (Figure 6 shows the PIN prompt). Brute force attacks, attempting to enter a correct PIN by testing many combinations until the correct one is found, are a general risk with such an authentication approach. This is something the SD Card can prevent in hardware. When configuring the card you can define the allowed number of incorrectly-entered PINs before the card will refuse further unlock attempts. Once the limit has been reached, a Supervisor PIN (which you have hopefully set and noted), can be used to unlock and change the SD card’s PIN. Otherwise, the card can no longer be unlocked.

USB Policy
The USB Policy enables an unattended secure boot. This works by adding a Swissbit PU-50n DP USB stick as a security token (Figure 3). The system is set up according to the user manual, where the SD card and the PU-50n DP USB stick are prepared with the same PIN. The PU-50n DP has the same secure firmware installed as the PS-45u DP. After the Raspberry Pi has been booted with the PS-45u DP SD card, a challenge-response authentication takes place and, if the PIN inside the PU-50n DP matches that inside the PS-45u DP, the boot process continues. A Raspberry Pi with this setup is shown in Figure 7. In Figure 8, a successful boot with an attached PU-50n DP USB stick is shown.


NET Policy
While PIN Policy and USB Policy allow for easy security retrofitting for standalone devices without network access, NET Policy is available for wired network devices. This requires the implementation of a license server inside the network that a Raspberry Pi with a PS-45u DP can use to unlock the SD card. A readymade Raspberry Pi image is provided for the license server and can be written to a standard 16 GB SD card. The license server runs on Raspberry OS and features a web interface for device configuration. The setup process is described in the Swissbit NetPolicyServer User Manual.
After boot up, the desktop starts and a connection can be made via a browser to https://localhost/NetPolicyServer/. This brings up the configuration webpage (Figure 9).

To add a device to the license server, the UID of the SD card you are activating, along with the corresponding password, is required. This information can be obtained from the Windows utility used for the SD card’s preparation. Following the guide for the SD card preparation an IP address (Figure 10) needs to be entered. Currently the system is limited to IPv4 networks. If you do not want to enter an IP address for your server, there is unofficial support for a DNS name instead, but this is not covered in the manual and should be used at your own risk.

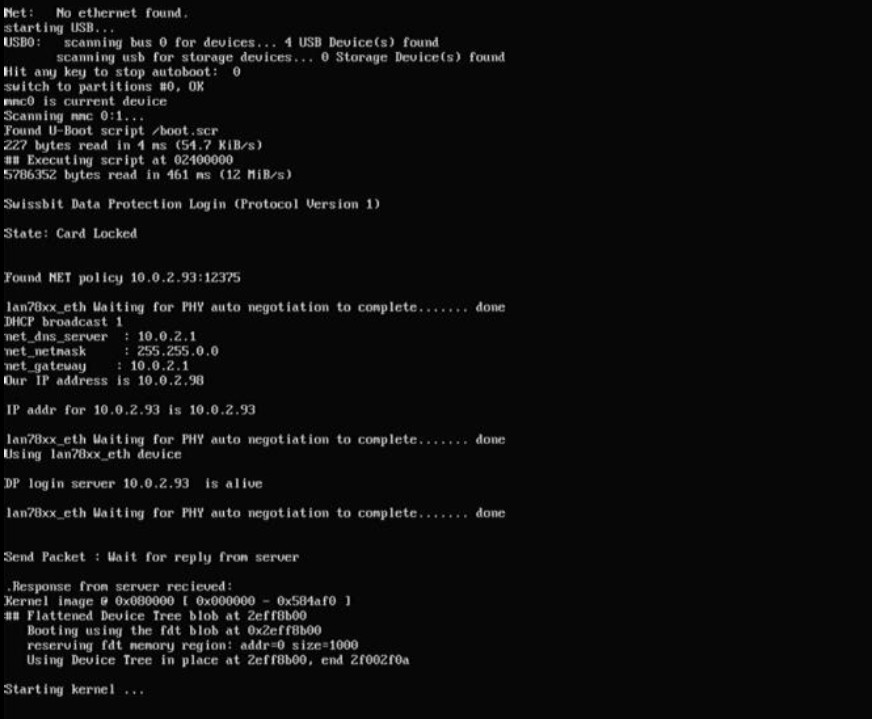
After the client has been configured, any boot attempt will contact the Net Policy Server. The Raspberry Pi and server will use a challenge-response scheme to unlock the SD card and, if the server doesn't provide the correct response or is not available, the boot process stops and the SD card remains locked. This centralized implementation allows the management of devices from the server, enabling them to be disabled in case they are no longer authorized to boot. Figure 11 shows the boot process with incorrect credentials set on the server side and a failed boot. Figure 12 shows the response for a successful boot.

Retrofit Existing Hardware
The advantage with retrofitting existing hardware is the simplicity of the process when replacing an SD card with the PS-45u DP ‘Raspberry Edition’. The examples and files provided assume that you are running a version of Linux on your device. This means an existing installation can be cloned once the files to enable the chosen PS-45u DP security features have been added according to the manual.
You could argue that the Pi should be able to do the same thing using software-based disk encryption but, sadly, on this platform all cryptographic operations must be performed in software. This results in a high processor load on the Raspberry Pi 2 and 3 during disk accesses, leading to performance bottle necks during the execution of standard applications. Because the PS-45u DP ‘Raspberry Edition’ implements the disc encryption within the integrated controller of the SD card, it offloads the encryption effort and has the additional benefit of not exposing the cryptographic keys. As a result, once the PS-45u DP is unlocked, the installed applications function as though they were on a normal SD card without any performance penalties. Depending on your application and chosen implementation policy, a security retrofit can be undertaken in a reasonable amount of time.
According to Swissbit, the “Raspberry Edition” was designed as a hands-on learning & evaluation kit to illustrate how secure boot functionality can be “upgraded” to embedded platforms that lack native support for it. For productive applications based on Raspberry, Swissbit recommends to use the ruggedized Raspberry Compute Module CM3+.
Wishes and final thoughts
The PS-45u DP ‘Raspberry Edition’ currently supports the Raspberry Pi 2 and 3 models as these are the most-used SoC versions (both for the standard and the compute modules). Those looking for support for the Raspberry Pi 4 need to wait until the required components are ready and tested. The same is also true for the NetPolicyServer, which can be considered a working tech demo rather than a fully-fledged and polished product. It would be nice to have some documentation on how to construct your own Net Policy Server along with background information on the protocols used rather than having to dig through the code. Also, those of us not using Windows would like to configure the PS-45u DP without the need for a virtual machine or dual-boot setup.
Despite these small wishes for a next-generation product release, this secure SD card's overall approach provides a simple way to protect data from unwanted access. The centralized network server for authentication is a further bonus, making it a great choice when retrofitting existing devices to add security. Not only does the PS-45u DP protect your data from being stolen, but it also restricts physical access to the Raspberry Pi's file system that would otherwise allow attackers to compromise the platform.


Discussion (0 comments)