Unlocking the Secrets of the eSIM and Cellular IoT (Elektor Engineering Insights)
on
If you’re new to cellular IoT, where do you start? The traditional SIM card is being replaced by an electronic alternative, the eSIM, and even being integrated into silicon as the iSIM. But that’s only part of the challenge. Security requirements and GDPR mean that security must be tackled as the architecture of your design is tackled. Joined by Kigen’s Toby Grimshaw and Zariot’s Jimmy Jones, Stuart Cording, the Electronics Reporter, explored how these two solutions come together in a recent episode of Elektor Engineering Insights ("Securing Cellular IoT with eSIM and iSIM").
SIMs are more than just an authentication chip — they are powerful devices that run complete applications. And while the traditional telecoms companies are mostly focused on smartphone users, there are partners like Kigen and Zariot who support the needs of cellular IoT users. Technologies like eSIMs and iSIMs allow us to ditch the plastic cards and deploy our devices with ease around the world, configuring them remotely through a process called provisioning. But, like with any technology, there are security challenges. Experienced partners not only understand what they are, they also offer solutions that mitigate those risks.
Is a SIM Just a “Dumb” Circuit?
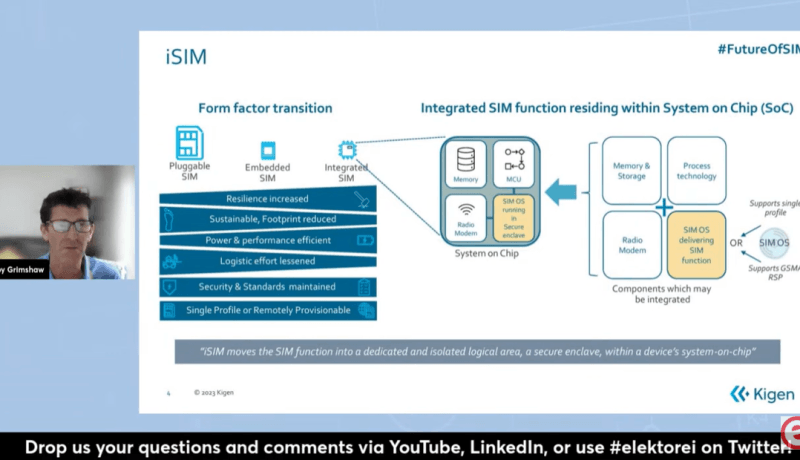
The conversation kicked off with a fundamental questions: What is a SIM card, and how does it work? Our first guest, Toby Grimshaw, explains that at its core, a SIM card contains a secure processor, often referred to as a tamper-resistant hardware element. This secure element is a standards-based component designed to protect sensitive data. On top of this secure processor, there’s an operating system that provides functional control to various apps and functionalities, including power-saving features. The SIM card also stores information about the subscriber’s profile, such as their subscription details. Depending on the type of device and its intended use, SIM cards may have different operating systems, including those designed specifically for consumer smartphones and others for IoT devices.
LTE-M and NB-IoT Devices
Next, our second guest, Jimmy Jones, explains the differences in how people should handle their SIM for LTE-M and NB-IoT, the two options in cellular IoT technology. In the IoT space, it’s essential to consider regional variations in cellular network support. Some regions primarily support Narrowband IoT (NB-IoT), like South Africa, while others, such as Central America, predominantly support LTE-M. There are also areas where both technologies coexist, like the UK, but even within these regions, specific carriers may prioritize one over the other. This network variability is crucial to keep in mind, especially for power efficiency, as NB-IoT is generally more power-efficient than LTE-M. It’s also worth noting that relying solely on older-generation networks like 2G and 3G as a backup strategy is becoming increasingly challenging due to network sunsets, with some regions already phasing out these older technologies. This evolving landscape requires careful consideration of your IoT device’s connectivity strategy, taking into account regional network priorities and the efficiency of your chosen technology.
eSIM and Cellular IoT: Q&As
Lastly, during the Q&A session, the guests addressed key questions, such as, a way for customers to try out an eSIM and iSIM. Toby explained that Kigen has valuable resources to share and will soon launch an integrated SIM evaluation kit program to make technology more accessible to the ecosystem. The experts also explained the significant role of blockchain in securing IoT devices and explored the possibility of growing of private networks in 5G for better control and scalability.
For those interested in the full episode and further information, jump over to Elektor TV - Industry or watch below:

Hey - I have a great story...
Great! We'd love to hear it. Feel free to get in touch to learn how to share your news with us. We'll try to squeeze it in somewhere, whether a product launch, new technology, breakthrough, or event. Simply contact Stuart Cording via email, on Twitter, or LinkedIn.


Discussion (0 comments)