Review: NXP EdgeLock® SE050E Secure Element
on
Once you dive into the topic of secure data connectivity and configuration (especially when it comes to products that are to be shipped pre-configured for cloud services), it’s very easy to get lost in all the information and technical requirements. The NXP EdgeLock SE050E Secure Element is one way to more easily implement such designs and products and harden them against data manipulation.
NXP EdgeLock SE050E Secure Element
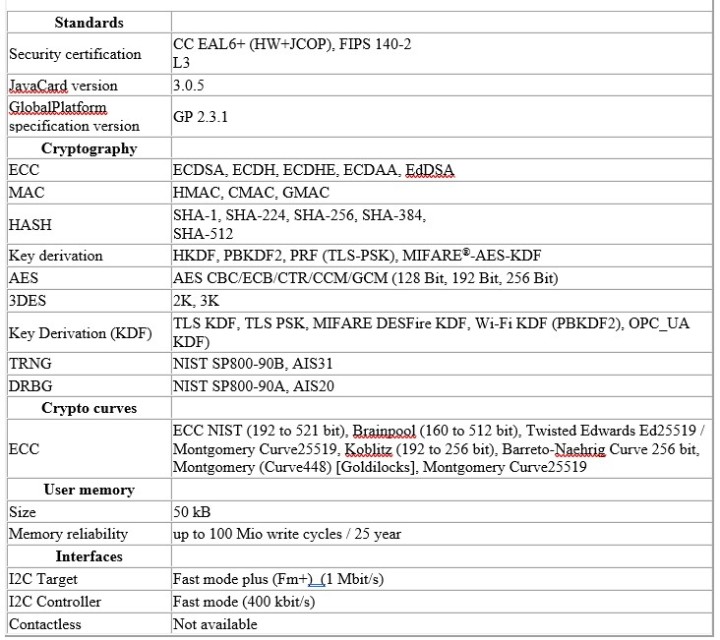
The EdgeLock SE050E Secure Element from NXP’s family of Plug & Trust devices offers advanced security features according to Common Criteria EAL 6+. The exact specifications of the SE050E Secure Element can be found in Table 1. To connect the SE050E Secure Element to a system, an I²C interface is sufficient. The chip’s supply voltage is listed as 1.62 V to 3.6 V, but the maximum for the chip is 6 V, which also allows it to be used in 5-V systems and makes the whole thing interesting as a retrofit option as well. Internally, the NXP EdgeLock SE050E is a small SoC (system on chip) with a Java Card OS and a dedicated IoT applet that ensures that not only cryptographic operations are performed securely. Attempts to unintentionally extract data from the chip are also detected and resisted. As root-of-trust, the SE050E Secure Element can thus be used to establish secure and trusted connections between two systems and to authenticate the systems.

Certificates please!
When it comes to secure communication between two partners, in this case IoT systems, most people will think of encryption; however, there is still one essential ingredient missing: In order for secure communication to work, both sides must trust each other and exchange keys. To achieve this, there are certificates. But what does such a certificate do?Let’s say there are two new employees who have never met before and are working out of their home offices. The two employees are Jim and Dave. Jim and Dave both work for Karen. Karen as their supervisor is trusted by Jim and Dave, and she has given Jim an assignment for Dave.
Jim gives the order from Karen to Dave, who now asks how he can be sure that the order really came from Karen. Karen has put a stamp on the document, which only Karen owns and which Jim and Dave know about. With a look at the stamp, Dave can thus verify that it is an order from Karen. In addition, both Jim and Dave check each other’s employee badges to make sure Jim is really Jim and Dave is really Dave. Karen has also put her stamp on these badges. In the hope that it was not too abstract, we now translate this into the digital world. The stamp that Karen used corresponds to a cryptographic key. As with such a stamp in an office, this cryptographic key must also be stored securely, ideally in a safe, otherwise anyone could take the stamp and place it on any documents. Put simply, for the cryptographic key, the NXP EdgeLock SE050E Secure Element assumes the function of the safe.
Jim becomes an IoT sensor that monitors a temperature, and Dave becomes a cloud provider, in this case Amazon AWS IoT. Karen from the example becomes a Certificate Authority (CA) that issues certificates instead of stamps.
As soon as the IoT sensor wants to send data to the cloud provider, the certificate of the cloud provider server is first checked by the sensor. The cloud provider’s server at this point also asks the sensor for its certificate to be sure that it is establishing communication with the correct instance. When both sides have verified that the identities are correct, an encrypted connection is started and the sensor can transmit its data.
Put simply, certificates are the identification documents of the digital world. However, since a certificate is a file that can be easily copied, certificates, like ID cards, have security features that are intended to prevent forgery. In the case of certificates, it is the cryptographic keys that serve as a security feature, like a stamp that cannot be forged. As in real life, identity theft and document forgery must be prevented in the digital world, too.
Secure certificate management
Those who use a Raspberry Pi for cloud-connected IoT applications, be it with Google Cloud Platform, Amazon Web Services, or Microsoft Azure, will have seen that suitable certificates must be installed on the Raspberry Pi in these cases. Each device can be assigned its own certificate, so that if a certificate is compromised, only one device is affected and not the entire fleet. Amazon has provided documents for this purpose, which explain this process. With a Raspberry Pi, however, the certificate and the cryptographic key would have to be stored on an SD card. The access data and the certificate could thus be copied easily.The EdgeLock SE050E Secure Element can remedy this situation by providing a secure environment for processing cryptographic keys and certificates. Up to 50 KB of memory can be used in the chip to store certificates and keys. While this may not sound like much in today’s times, considering gigabyte-sized USB flash drives, it does mean that a large number of certificates can be stored in the EdgeLock SE050E Secure Element. But the chip is more than just a secure key storage. If you take a look at the chip’s connection, you will see that it is implemented via I²C. With the EdgeLock SE050E Secure Element, the I²C communication between the chip and the host can also be encrypted, so that the chip and host are bound to each other. NXP has provided an application note (AN12662) for this purpose. Thus, the EdgeLock SE050E Secure Element can not only securely store cryptographic keys and other confidential data and protect them from unwanted extraction, but also provide secure encrypted communications.
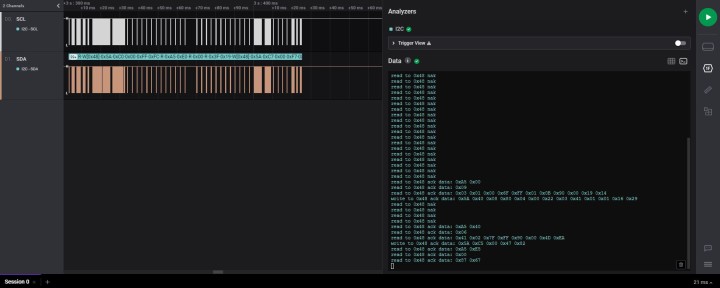
Other variants of the EdgeLock family additionally offer connections for NFC as well as an I²C controller interface and thus allow for very interesting applications. With the compatible chip variants, NFC can be used to transfer data into chips of the EdgeLock family very late during production or even shortly before delivery. An NFC-enabled device, such as a smartphone, thus allows certificates and configurations to be transferred to the chip without direct electrical contact with the circuit board. For this purpose, the chip is supplied with energy by the NFC-enabled device; the actual system does not have to be active for the configuration.
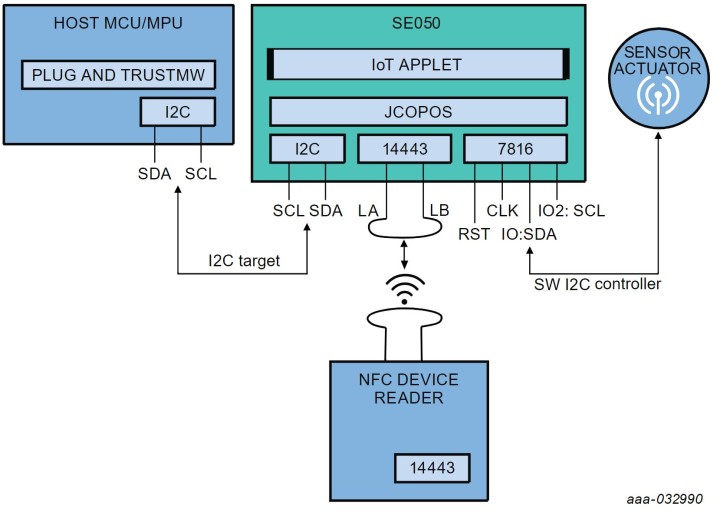
Interfaces of the EdgeLock SE05x family (Source: https://www.nxp.com/docs/en/data-sheet/SE050-DATASHEET.pdf)
A practical example
In the following example, the EdgeLock SE050E Secure Element is used in conjunction with a Raspberry Pi 4. The SoC of the Raspberry Pi 4 has not only found its way into commercial products as a small single-board computer, but also through the Compute Module 4. Even though it may be difficult to obtain Raspberry Pi products at the moment, they are a very good platform to couple with an EdgeLock SE050E Secure Element due to their widespread use. A Raspberry Pi Zero 2W can be perfectly combined with an EdgeLock SE050E Secure Element as well. An application note on how to get the EdgeLock SE050E Secure Element up and running with the Raspberry Pi can be found in AN12570.What will be shown in this example is the use of a cloud service, Amazon AWS IoT Core in this case, where the EdgeLock SE050E Secure Element is used for authentication and onboarding. Since the Raspberry Pi has to exchange data with the Amazon AWS, it will log into a Wi-Fi network. However, this is not done with a pre-shared key (WPA2-PSK), but using a certificate with WPA2-EAP. Thus, no Wi-Fi key is stored on the SD card of the Raspberry Pi that could be read later. The same applies to the certificate used for Amazon AWS IoT Core. This is not stored on the SD card either, so it cannot be copied simply by accessing the file system.
Hardware for a test run
For the test setup, a Raspberry Pi 4 is equipped with an EdgeLock SE050 Arduino Compatible Development Kit (OM-SE050ARD-E) and the OM-SE050RPI ARDUINO to Raspberry Pi Adapter Board (OM-SE050RPI).
A Raspberry Pi 4 with the latest Raspberry Pi OS (32 bit) is used. For WPA2-EAP, an access point and a FreeRadius server (can run on the access point) are provided. So, not much hardware is needed for the first tests.

WPA2-EAP setup
The setup is similar to the one shown in the video “Wi-Fi Credential Protection with EdgeLock SE050” from NXP, and all steps for the configuration can be found in the application note AN12661 from NXP. The setup details for the Raspberry Pi and the access point can be found in the video on WPA2-EAP and the EdgeLock SE050E Secure Element.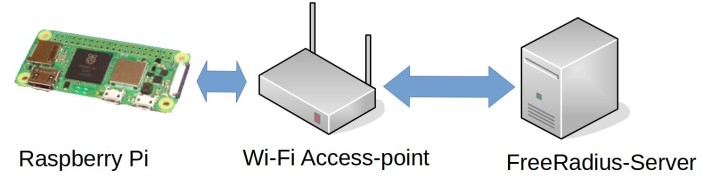
The Raspberry Pi uses the EdgeLock SE050E Secure element to connect to the Wi-Fi network. The access point forwards the connection request to the FreeRADIUS server, which checks whether this Raspberry Pi is trustworthy with its certificates. The FreeRADIUS server then informs the access point whether the Raspberry Pi is authorized to connect to the Wi-Fi network, what rights it has in the network, which VLAN it is assigned to, and other optional parameters. This procedure is especially useful for centrally managed Wi-Fi networks, as it allows the Raspberry Pi to log in to different access points and no Wi-Fi passwords need to be stored on the SD card.
Unfortunately, the firmware of the Wi-Fi module installed on the Raspberry Pi 4 has caused problems with WPA2-EAP in the past. If the Wi-Fi example does not work, this is not necessarily due to a misconfiguration. Depending on the access point model, there might also be occasional bugs in connection with WPA2-EAP.
Video: Wi-Fi Credential Protection with EdgeLock SE050 (Quelle: NXP).
The video from NXP shows step by step how to set up WPA2-EAP with an OpenWRT-based access point and is a good supplement to the application note AN12661.
Amazon AWS IoT Core
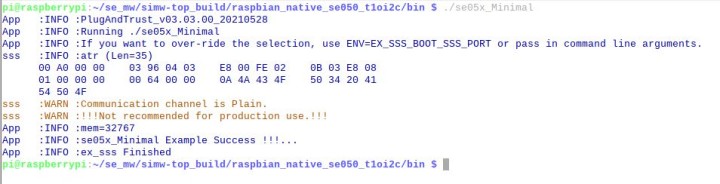
Something that should be checked first is the correct time and the reachability of an NTP server from the Raspberry Pi. If the Raspberry Pi cannot reach an NTP server and the time is not set, a TLS error may occur.The secure connection of sensors and actuators to a cloud platform can be done with the EdgeLock SE050E Secure Element with manageable effort and in reasonable time. For this purpose, the aws_eou demo from the middleware of the EdgeLock SE050E Secure Element can be tried out. The necessary steps for the configuration are described in the Knowledge Base about the SE05x family.
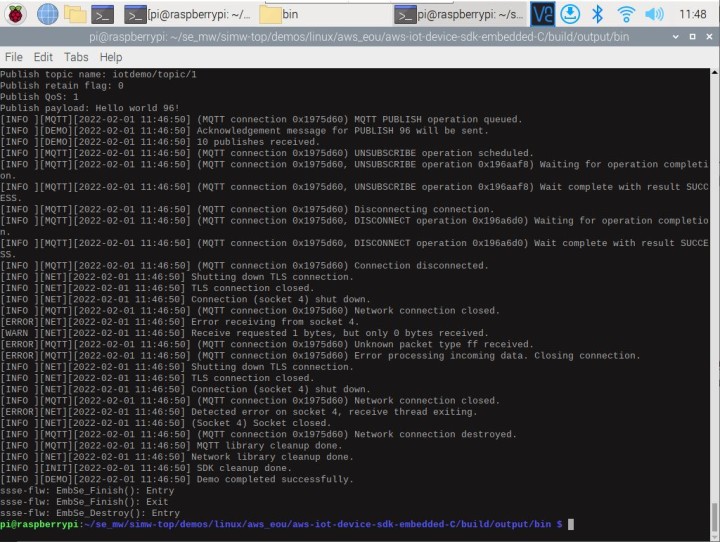
Once the IoT demo from the example is run, the messages also appear in the Amazon AWS IoT Core and can be viewed under
Test using the MQTT client. To see the messages, the topic # must be subscribed to with the MQTT client.
This is a demonstration of how to securely transport data to the cloud with the EdgeLock SE050E Secure Element. It doesn’t even have to be AWS, other cloud solutions can be used with the EdgeLock SE050E Secure Element as well.
More use cases than expected
Although cloud services from large vendors are playing an increasingly important role in the IoT world, the EdgeLock SE050E Secure Element is not limited to them. NXP provides a wide range of application notes for the EdgeLock SE050E Secure Element, e.g. for use as a TPM-like module, device-to-device authentication, securing the boot sequence of microcontrollers or for configuration via NFC. ISA/IEC 62443 compliance can also be achieved with the EdgeLock SE050E Secure Element with little effort.A companion for microcontrollers and small board computers
The example above shows the EdgeLock SE050E Secure Element in combination with a Raspberry Pi 4 and some of its possible applications. However, the EdgeLock SE050E Secure Element is also an excellent addition to smaller microcontrollers, such as a Raspberry Pi Pico with Ethernet Shield or the Wiznet W7500. These microcontrollers are able to establish encrypted connections to cloud services. However, the cryptographic functions required for authentication and thus for establishing the connection are very computationally intensive. What is done within a few milliseconds with a Raspberry Pi 4 and its four ARM Cortex cores can cost smaller microcontrollers times in the range of seconds. Here, the EdgeLock SE050E Secure Element can take considerable work off the small microcontrollers, which is not only a security gain. The computing time required for data exchange can also be significantly reduced, which in turn reduces energy consumption.Simple integration with few components
As with all chips introduced into a project, there is always the question how many components are needed around the actual chip. In the case of the Raspberry Pi, it is three passive components, two pull-up resistors for I²C and an optional 100 nF blocking capacitor. This allows for an easy and space-saving integration into new designs, be it a Raspberry Pi or an MCU. An inexpensive way to start developing a project that uses a chip from the EdgeLock SE05x family would be the Plug&Trust Click from MikroElektronika. Due to the simple circuitry of the EdgeLock SE050E Secure Element, it would not be surprising if a module with a Groove or Qwiic connector would be introduced, which could be connected to existing evaluation boards with the simplest of means.Summary
Anyone new to the topic of IoT, certificates, root-of-trust, and Secure Elements should first work through a bit of theory. “Plug and Trust” for the EdgeLock SE050E Secure Element is very true, but it should not be confused with “Plug and Play”. The EdgeLock SE050E Secure Element allows for highest security in IoT applications with few components. For setup and operation, NXP provides appropriate documentation to help users achieve their security requirements through appropriate configuration, but any security element is only as good as its integration into the respective application. With the EdgeLock SE050E Secure Element, you not only have access to the documentation from NXP, but you can also ask for help from a European-based manufacturer.
For those who use a Raspberry Pi 4 or a Compute Module 4, the EdgeLock SE050E Secure Element is a useful addition. The simple connection via I²C makes hardware and software integration possible in just a few steps. When using an MCU, not only can the security of the application be increased, the EdgeLock SE050E Secure Element can also help reduce energy consumption. With the EdgeLock SE050E Secure Element, more options to increase system security are available with fewer components and effort than one might first think.
Translation: Jörg Starkmuth


Discussion (0 comments)