| Most of your customers are serious about embedded security, so you must test your products for security vulnerabilities to protect them from...
More about Security (153)
| Arcs in electrical installations are usually the result of loose contacts or damage to cables and conductors. To reduce the risk of a fire,...
| Messages can be encrypted to prevent their contents to be intercepted or altered. However, to read the message the intended receiver must be...
| A simple device for secure transportation of OTP keycards, solves the problem of secure distribution of encryption keys. Tampering will be d...
| Microchip announces the new SAM L10 and SAM L11 families of 32-bit microcontrollers (MCUs) which address the growing need for security in In...
| Mobile devices such as smartphones are currently protected from improper use by a password, swipe gesture and fingerprint or face recognitio...
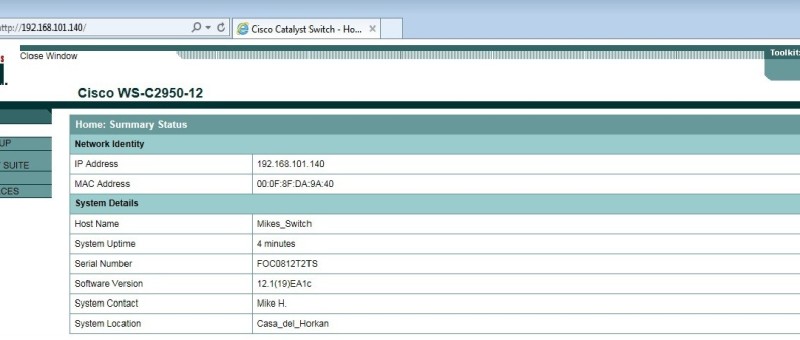
| When a piece of hardware is insecure and may become a potential target for malware attacks, things become complicated. When a vulnerability...
| For little cost it is possible to add the GT-521F52 fingerprint scanner with a serial interface to a microcontroller, an Arduino, a Raspberr...
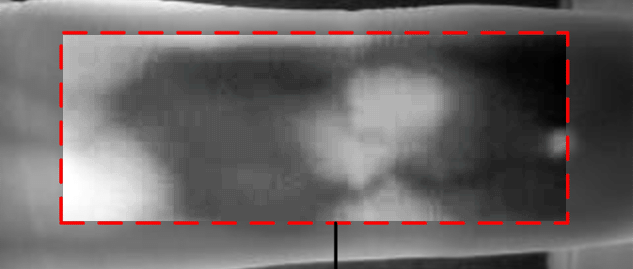
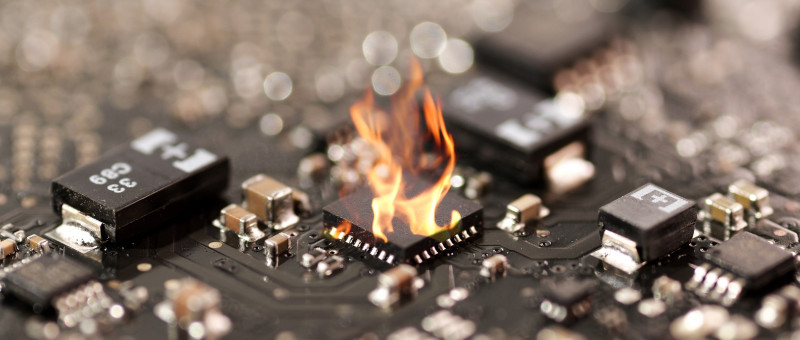
| A thermal runaway is an increasing threat to electronic devices where more and more power is packed in ever smaller spaces; it is a threat t...
| Microchip announces the ATECC608A CryptoAuthentication™ device, a secure element that allows developers to add hardware-based security to th...